Fahid Dec 6, 2025 3
Network scanning is a core skill for Certified Ethical Hacker candidates. This c...
Fahid Nov 3, 2025 17
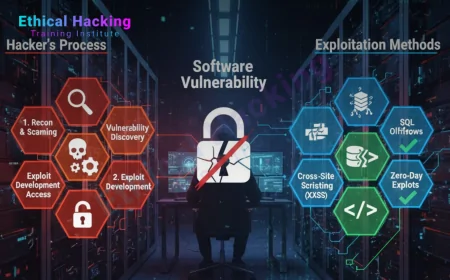
Software vulnerabilities are flaws in code, configuration or design that attacke...
Fahid Nov 1, 2025 4.5k
Aayushi May 15, 2025 2k
Aayushi Jun 20, 2025 819
Aayushi Jun 23, 2025 479