What Are the CEH Hacking Phases Explained for Beginners?
2025-2026 simple explanation of the 5 CEH hacking phases for beginners. Reconnaissance, Scanning, Gaining Access, Maintaining Access, Clearing Tracks with real examples, tools, labs and how Ethical Hacking Training Institute teaches all phases with 500+ live targets for practical mastery.
Introduction
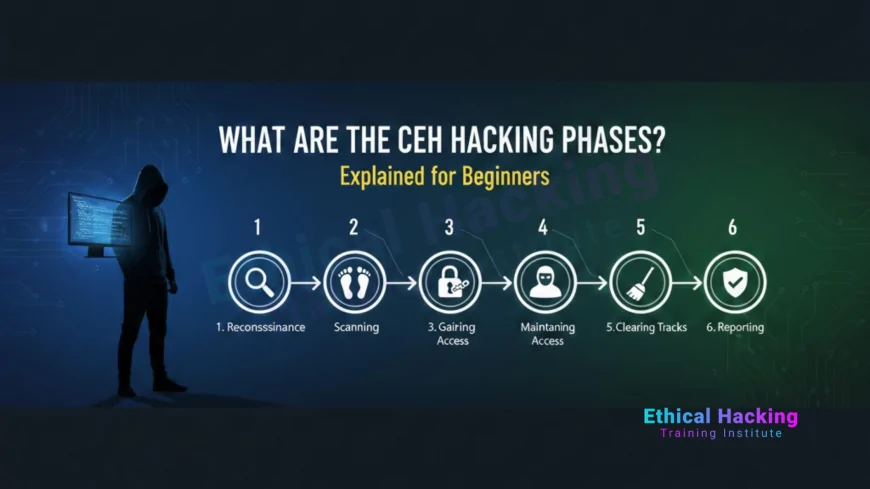
The CEH certification is built around the 5-phase hacking methodology that real attackers follow. These phases are tested in both theory (10–15 questions) and practical (every flag belongs to one phase). Beginners often skip phases or use wrong tools, leading to low scores. At Ethical Hacking Training Institute we teach the phases with real-world examples and 500+ live targets so students understand the complete flow and score full marks in CEH practical.
Overview of the 5 CEH Hacking Phases
| Phase Number | Phase Name | Main Goal | Key Tools |
|---|---|---|---|
| 1 | Reconnaissance | Gather information | Google dorks, Maltego, theHarvester |
| 2 | Scanning | Find vulnerabilities | Nmap, Nessus, Nikto |
| 3 | Gaining Access | Exploit & enter | Metasploit, sqlmap, Burp Suite |
| 4 | Maintaining Access | Stay inside | Netcat, Meterpreter persistence |
| 5 | Clearing Tracks | Hide evidence | Log deletion, timestomp |
Understand the 5 phases flow.
Reconnaissance Phase – Information Gathering
- Passive: Google dorks, WHOIS, Shodan
- Active: DNS queries, subdomain brute
- Collect emails, employees, tech stack
- Our lab has 200+ real domains daily
Scanning Phase – Vulnerability Discovery
Use Nmap for port scanning, Nessus for vulnerability scanning, Nikto for web servers. This phase finds open doors and weak points. Our daily scanning challenges cover all tools and techniques.
Scan with Nmap.
Gaining Access Phase – Exploitation
- Web: SQLi, XSS, CSRF
- System: Metasploit exploits
- Network: password cracking
- Social engineering: phishing
- Our lab has 200+ exploitable targets
Maintaining Access Phase – Persistence
- Backdoors with Netcat
- Meterpreter persistence
- Registry/cron jobs
- Rootkits for hiding
- Our lab tests persistence daily
Maintain access with backdoors.
Clearing Tracks Phase – Cover Your Presence
- Delete logs & history
- Timestomp files
- Disable auditing
- Remove created users
- Our forensic lab checks tracks
Conclusion
The 5 phases form the complete hacking methodology. Join Ethical Hacking Training Institute and get:
- 500+ live targets covering all phases
- Daily mock practicals
- Weekend & weekday batches
- 100% placement support
Book free demo — start phase 1 today!
Avoid common mistakes.
Frequently Asked Questions
How many phases are in CEH?
5 standard phases.
Which phase is most important?
Reconnaissance — foundation of everything.
Is phase 5 tested in practical?
Yes — clearing tracks flags.
Is social engineering a separate phase?
No — part of gaining access.
Do you teach all 5 phases?
Yes — complete methodology.
Is reconnaissance only passive?
No — active too.
Is scanning phase easy?
Yes — Nmap makes it simple.
Weekend batch covers phases?
Yes — full coverage.
How many flags follow phases?
All 20 flags belong to phases.
Is reporting separate?
Yes — after phase 5.
Can freshers understand phases?
Yes — we explain with examples.
Is lab for all phases?
Yes — 500+ targets.
Is phase order important?
Yes — always 1 to 5.
Do you give phase cheat sheet?
Yes — tools & techniques per phase.
How to start today?
Book free demo — learn first phase!
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0

















