What Skills Are Required to Learn Ethical Hacking?
Curious about becoming an ethical hacker? This complete beginner-friendly guide reveals the essential technical and soft skills needed to learn ethical hacking, from networking basics to problem-solving mindset, with practical learning paths and free resources.
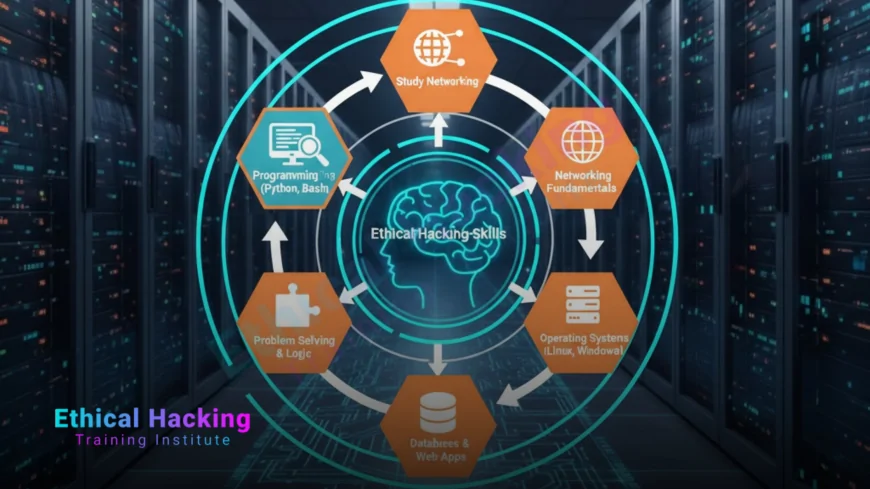
Introduction: Why Ethical Hacking Matters Today
Cybercrime costs the world trillions annually. Companies, governments, and individuals face constant digital threats. Ethical hackers, also known as white-hat hackers, help protect systems by finding vulnerabilities before malicious actors do.
Ethical hacking combines technical expertise, creative thinking, and strong ethics. Professionals in this field work with permission to test security, report weaknesses, and recommend fixes. Demand for skilled ethical hackers continues to rise as organizations prioritize cybersecurity.
This guide breaks down every skill you need to start learning ethical hacking. Whether you aim for a career in penetration testing or simply want to understand digital security better, these foundations apply universally. Explore the best CEH courses to kickstart your journey.
Understanding the Ethical Hacking Mindset
Technical tools matter, but mindset comes first. Ethical hackers think like attackers while staying within legal and moral boundaries.
Key Mental Traits
- Curiosity: You explore how systems work and break
- Persistence: Solutions rarely appear instantly
- Attention to detail: One misconfiguration can create a vulnerability
- Ethical integrity: You never exploit findings for personal gain
- Continuous learning: Technology evolves daily
Legal and Ethical Boundaries
Always obtain written permission before testing any system. Unauthorized access, even with good intentions, remains illegal. Join bug bounty programs or use legal lab environments for practice.
Core Technical Skills: Building Your Foundation
Start with these fundamental areas before touching advanced tools.
Computer Networking Essentials
Understanding data flow forms the backbone of hacking knowledge.
- TCP/IP model and OSI layers
- IP addressing, subnetting, and CIDR notation
- Common protocols: HTTP, DNS, FTP, SSH
- Packet analysis with Wireshark
- Network devices: routers, switches, firewalls
Operating Systems Mastery
Linux dominates penetration testing environments.
Linux Command Line Proficiency
| Category | Essential Commands | Purpose |
|---|---|---|
| File Management | ls, cd, pwd, mkdir, rm, cp, mv | Navigate and manipulate files |
| Process Control | ps, top, kill, bg, fg | Monitor and manage running programs |
| Network Tools | ping, netstat, ifconfig, nmap, curl | Test connectivity and scan systems |
| Text Processing | grep, awk, sed, cat, sort | Search and manipulate data streams |
| Permissions | chmod, chown, sudo, su | Control access and elevate privileges |
Programming Skills for Ethical Hackers
Code understanding enables automation and exploit development.
Python: The Hacker's Swiss Army Knife
Learn Python for its readability and vast security libraries.
- Script network scanners and brute forcers
- Automate repetitive testing tasks
- Parse logs and analyze data
- Build custom exploitation tools
Bash Scripting Basics
Create one-liners and automation scripts directly in terminal.
- Chain commands with pipes and redirects
- Use loops and conditionals
- Handle files and variables
- Schedule tasks with cron
Web Technologies Understanding
Most vulnerabilities exist in web applications.
- HTML, CSS, and JavaScript basics
- HTTP request/response structure
- Cookies, sessions, and authentication
- Common web vulnerabilities: SQL injection, XSS, CSRF
Security Concepts and Tools
Master the methodology before the tools.
Ethical Hacking Phases
- Reconnaissance: Gather target information
- Scanning: Identify live systems and services
- Gaining access: Exploit vulnerabilities
- Maintaining access: Establish persistence
- Covering tracks: Remove evidence of intrusion
Essential Tool Categories
- Information gathering: theHarvester, Maltego
- Network scanning: Nmap, Masscan
- Vulnerability scanning: Nessus, OpenVAS
- Password cracking: Hashcat, John the Ripper
- Web application testing: Burp Suite, OWASP ZAP
- Exploitation frameworks: Metasploit
Among scanning tools, mastering Nmap proves essential for every ethical hacker.
Soft Skills That Set Great Hackers Apart
Technical ability opens doors. These skills keep you employed.
Problem-Solving and Logical Thinking
Approach challenges systematically. Break complex problems into smaller, testable components. Practice with Capture The Flag (CTF) challenges on platforms like HackTheBox or TryHackMe.
Communication and Reporting
Technical teams and executives need clear explanations.
- Write detailed vulnerability reports
- Explain risk levels in business terms
- Document findings reproducibly
- Present recommendations effectively
Research and Self-Learning
New vulnerabilities emerge daily. Stay current through:
- Security blogs and podcasts
- Vulnerability databases (CVE, NVD)
- Conferences and local meetups
- Online communities and forums
Building Your Learning Path
Follow this structured roadmap to progress efficiently.
Months 1 to 3: Foundations
- Complete basic networking course
- Install Kali Linux in virtual machine
- Master 50+ Linux commands
- Learn Python fundamentals
- Understand web application flow
Months 4 to 6: Core Skills
- Practice Nmap scanning techniques
- Study common web vulnerabilities
- Complete beginner CTF challenges
- Learn Burp Suite basics
- Write simple exploitation scripts
Months 7 to 12: Specialization
- Choose focus area: web apps, networks, mobile
- Join bug bounty programs
- Pursue CompTIA Security+ certification
- Build home lab with vulnerable machines
- Contribute to open-source security projects
Intensive training through an ethical hacker bootcamp can accelerate your progress significantly.
Certifications to Validate Your Skills
Credentials demonstrate competence to employers.
- CompTIA Security+: Entry-level security knowledge
- CEH (Certified Ethical Hacker): Practical methodology
- eJPT: Hands-on junior penetration tester
- OSCP: Advanced practical penetration testing
- CompTIA PenTest+: Mid-level penetration testing
Practice Environments and Resources
Legal practice makes perfect.
Free Learning Platforms
- TryHackMe: Gamified learning paths
- HackTheBox: Realistic penetration challenges
- OverTheWire: Command-line wargames
- PortSwigger Web Security Academy: Web vulnerabilities
- PentesterLab: Targeted exercise bundles
Building Your Lab
Set up virtual machines with:
- Kali Linux (attacker)
- Metasploitable (vulnerable target)
- Windows 10/11 (common client OS)
- DVWA (Damn Vulnerable Web Application)
Many aspiring hackers choose to learn ethical hacking from home using structured online programs.
Conclusion: Start Your Ethical Hacking Journey Today
Learning ethical hacking requires dedication across multiple domains: networking, operating systems, programming, security concepts, and soft skills. Begin with strong foundations in Linux and networking, then progressively add tools and techniques through structured practice.
The field rewards persistent learners who combine technical depth with ethical responsibility. Every expert started as a beginner. Install your first virtual machine, complete your first CTF challenge, and join the community of security professionals making the digital world safer.
Your skills can protect organizations and individuals from real threats. Start small, stay consistent, and watch your capabilities grow into a rewarding career in cybersecurity. For hands-on validation, prepare for the CEH practical exam and understand the importance of CEH certification in your career.
Frequently Asked Questions
Do I need a degree to learn ethical hacking?
No degree required. Many successful ethical hackers are self-taught. Certifications and demonstrated skills matter more to employers than formal education.
How long does it take to learn ethical hacking?
Basic proficiency takes 6 to 12 months of consistent study. Professional-level skills require 2 to 3 years of practice and real-world experience.
Is ethical hacking legal?
Yes, when you have explicit written permission from system owners. Unauthorized access remains illegal regardless of intent.
Can I learn ethical hacking without programming?
Basic hacking possible without coding, but programming knowledge significantly expands capabilities and automation potential.
What computer do I need for ethical hacking?
Any modern laptop with 8GB+ RAM and virtualization support works. Use virtual machines to run Kali Linux and target systems safely.
Should I learn Kali Linux or regular Linux first?
Learn Ubuntu or Debian first for Linux fundamentals. Kali contains pre-installed tools but assumes Linux proficiency.
Are bug bounty programs good for beginners?
Start with educational platforms first. Bug bounties require solid fundamentals to avoid frustration and account suspensions.
How much do ethical hackers earn?
Entry-level positions start around $70,000 annually. Experienced penetration testers earn $120,000+ with specialized skills and certifications.
Is Python or Bash more important for hacking?
Learn both. Python enables complex tool development. Bash handles quick terminal automation and system interaction.
Can I practice hacking on my own network?
Yes, create isolated virtual networks for practice. Never test on production systems or networks without authorization.
What is the difference between ethical and malicious hacking?
Intent and permission. Ethical hackers have authorization and aim to improve security. Malicious hackers exploit without consent for personal gain.
Should I learn wireless hacking as a beginner?
Focus on core skills first. Wireless security builds on networking knowledge and requires specific hardware for practice.
How important are CTF challenges?
Extremely valuable. CTFs develop practical problem-solving across multiple domains in realistic scenarios.
Do I need to know assembly language?
Not for beginners. Assembly becomes relevant for reverse engineering and low-level exploit development at advanced levels.
How can I stay updated with new vulnerabilities?
Follow security researchers on social platforms, subscribe to vulnerability feeds, and participate in community discussions regularly.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0

















