What Is Social Engineering in Cybersecurity?
Learn what social engineering is, how attackers manipulate human psychology to breach systems, and real-world examples in 2025. This beginner-friendly guide explains phishing, vishing, baiting, and more, plus how to protect yourself and your organization with training from the Ethical Hacking Institute.
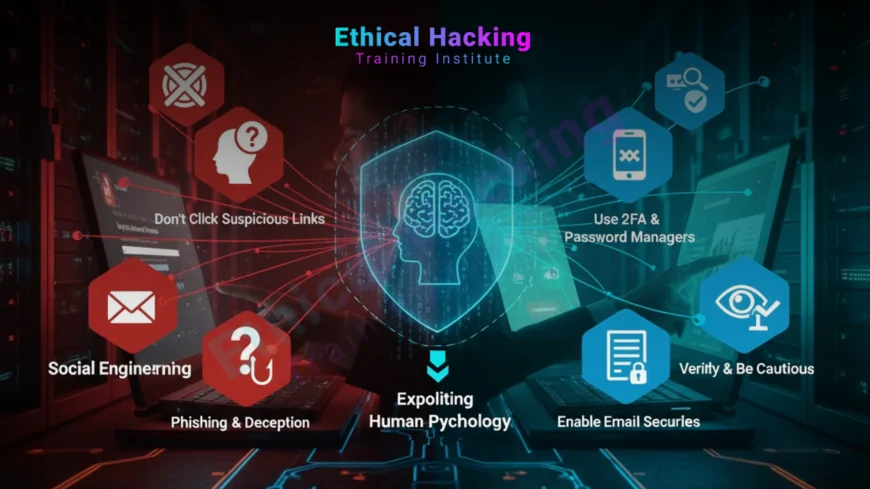
Introduction
In cybersecurity, the weakest link isn’t always code or firewalls. It’s people. Social engineering is the craft of exploiting human psychology to trick individuals into revealing sensitive information, clicking malicious links, or granting unauthorized access.
Unlike traditional hacking, social engineering doesn’t require advanced coding. It uses trust, fear, urgency, and curiosity, the same tactics used in scams for centuries, now supercharged with digital tools. In 2025, with AI deepfakes and voice cloning, these attacks are more convincing than ever.
This guide breaks down what social engineering is, how it works, real-world examples, and simple steps to defend against it. Whether you're a student, employee, or business owner, understanding this threat is your first line of defense.
Definition: What Exactly Is Social Engineering?
Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables. In cybersecurity, attackers use psychological tricks to bypass technical defenses.
Core Principles
- Trust: Pretending to be someone you know or respect
- Urgency: Forcing quick decisions without thinking
- Fear: Threatening consequences (e.g., “Your account will be deleted”)
- Curiosity: Offering something irresistible (free gift, urgent update)
- Authority: Impersonating bosses, IT, or law enforcement
It’s not about breaking systems. It’s about breaking people.
Types of Social Engineering Attacks
Here are the most common methods used in 2025:
| Type | Method | Example |
|---|---|---|
| Phishing | Fake emails/texts with malicious links | “Reset your password now” from “bank” |
| Vishing (Voice Phishing) | Phone calls pretending to be support | “Your account is compromised, give me the code” |
| Smishing (SMS Phishing) | Text messages with urgent links | “Your package is held, click to release” |
| Pretexting | Creating a fake scenario | “I’m from HR, need your login for audit” |
| Baiting | Leaving infected USB in parking lot | “Confidential Files” drive plugged in |
| Tailgating | Following into secure area | Holding door with fake badge |
Phishing alone causes 90 percent of data breaches.
How Social Engineering Works: Step-by-Step
Attackers follow a playbook:
- Research: Gather info from LinkedIn, company sites, social media
- Build Trust: Create believable identity or story
- Exploit Emotion: Use fear, greed, or urgency
- Request Action: Ask for password, click link, transfer money
- Cover Tracks: Delete evidence, move laterally
Example: A hacker emails “IT Support” saying, “Urgent system update required. Click here or lose access.” Employee clicks, malware installs.
Learn to spot these in an ethical bootcamp at the Ethical Hacking Institute.
Real-World Examples of Social Engineering
These famous cases show the power of manipulation:
Twitter Hack (2020)
Teenagers used vishing to trick Twitter employees into giving admin access. They hijacked accounts of Obama, Elon Musk, and Apple.
Ubiquiti Breach (2021)
Attacker posed as colleague, convinced finance to wire $46 million via email spoofing.
Deepfake CEO Scam (2023)
AI voice clone of CEO ordered employee to transfer $250,000 in a video call.
In 2025, AI makes these attacks nearly undetectable.
Why Social Engineering Is So Effective
Humans are wired to trust. Key psychological triggers:
- Reciprocity: “I helped you, now help me”
- Scarcity: “Limited time offer”
- Social Proof: “Everyone is doing it”
- Authority Bias: Obeying perceived leaders
Even tech-savvy people fall for well-crafted attacks. 98 percent of cyber attacks rely on social engineering.
Train your team with CEH practical simulations at the Ethical Hacking Institute or Cyber Security Institute.
Emerging Threats in 2025: AI and Deepfakes
Technology amplifies social engineering:
AI Voice Cloning
Clone a boss’s voice with 30 seconds of audio. Call finance: “Approve this wire transfer now.”
Deepfake Video
Fake Zoom call with realistic face and voice. Used in whaling attacks on executives.
Personalized Phishing
AI scrapes your social media to craft hyper-targeted emails: “Remember our chat at DEF CON?”
Defense: Verify identity via secondary channel (e.g., in-person or encrypted app).
How to Protect Yourself and Your Organization
Build a “human firewall” with these steps:
Individual Tips
- Never click unsolicited links
- Verify requests via phone or in-person
- Use password manager and 2FA
- Shred sensitive documents
- Lock your screen when away
Organizational Defenses
- Regular security awareness training
- Simulated phishing campaigns
- Zero-trust policies
- Email filters and link scanners
- Physical security (badges, no tailgating)
Webasha Technologies offers enterprise training to reduce click rates by 80 percent.
Tools Used by Social Engineers (And Ethical Testers)
Both attackers and pentesters use:
- Social Engineering Toolkit (SET)
- Maltego (OSINT gathering)
- GoPhish (phishing simulations)
- Deepfake software (ElevenLabs, Respeecher)
Ethical hackers use these in controlled tests to expose weaknesses.
Master these tools legally with CEH online at the Ethical Hacking Institute.
Conclusion: The Best Defense Is Awareness
Social engineering proves that technology alone can’t secure systems. People must be trained, skeptical, and prepared.
In 2025, with AI making attacks indistinguishable from reality, awareness is your strongest shield. Start with simple habits: pause, verify, report. For businesses, invest in training from the Ethical Hacking Institute, Cyber Security Institute, or Webasha Technologies.
Remember: If something feels off, it probably is. Trust your gut, protect your data.
Frequently Asked Questions
Is social engineering illegal?
Yes, when used to steal or harm. Ethical testing with permission is legal.
Can antivirus stop social engineering?
No. It blocks malware, not human manipulation.
Who is most vulnerable?
New employees, non-technical staff, and executives (whaling).
How do I report a phishing email?
Forward to [email protected] or your IT team. Delete after.
Can 2FA stop social engineering?
It helps, but attackers use SIM swapping or session hijacking.
Is tailgating still common?
Yes, especially in hybrid offices. Always challenge strangers.
Do deepfakes work on video calls?
Yes, but lag and lighting can give clues. Use passphrases.
Can I train to resist social engineering?
Yes. Role-playing and simulations build immunity.
What’s the difference between phishing and spear phishing?
Phishing is mass; spear phishing targets one person with personal info.
Is Kevin Mitnick still active?
He passed in 2023, but his techniques live on in training.
Can AI detect social engineering?
Partially. It flags suspicious patterns, but humans must verify.
Should I confront a tailgater?
Politely ask for ID. Never risk safety.
Are USB drops effective?
Yes. 48 percent of people plug in found drives (study).
Where can I learn ethical social engineering?
CEH, OSCP, or bootcamps at the Ethical Hacking Institute.
How often should we train staff?
Quarterly simulations + annual full training.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0


















