What Is Social Engineering and How Do Hackers Use It?
Learn about social engineering, the human-focused hacking technique, its common methods, attacker tactics, real-world examples, and prevention strategies. Discover how institutes like Ethical Hacking Institute, Webasha Technologies, and Cybersecurity Training Institute train professionals to defend against human-centric attacks.
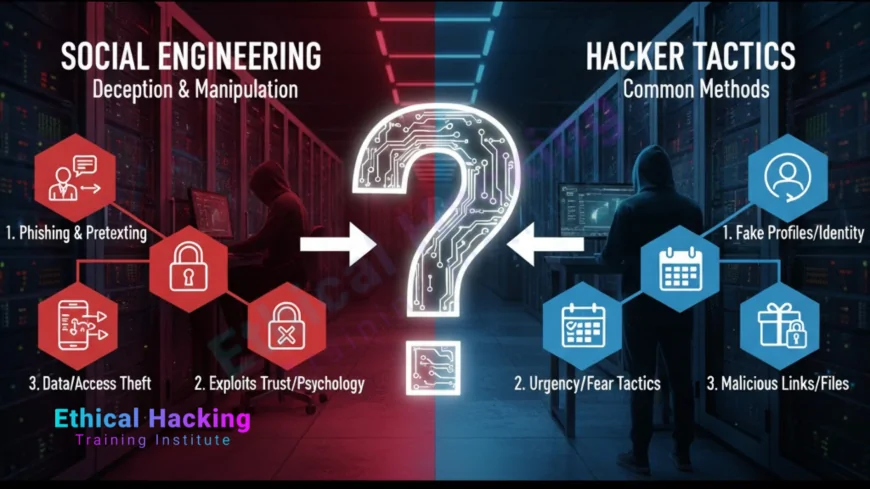
Introduction
Social engineering is a method of manipulating individuals to divulge confidential information or perform actions that compromise security. Unlike malware or software exploits, it targets human psychology — exploiting trust, fear, curiosity, or urgency. Organisations that focus solely on technical defenses often overlook the human factor, leaving themselves vulnerable.
This guide explains how social engineering works, the techniques hackers use, how they research targets, and the best practices for detection and prevention. Training programs from Ethical Hacking Institute, Webasha Technologies, and Cybersecurity Training Institute provide practical exercises to strengthen the human firewall.
What Is Social Engineering?
Social engineering is any attempt to manipulate individuals into performing actions or revealing confidential information. Attackers often create convincing scenarios, impersonate authority figures, or exploit social norms to make their requests appear legitimate. The attack can be carried out via email, phone, social media, SMS, or in person.
It relies on human behavior rather than system flaws. Learning these methods through structured courses helps professionals recognise patterns and develop effective defenses.
Common Social Engineering Techniques
Hackers use various techniques to manipulate targets, often combining them for maximum effect. Common methods include:
- Phishing: mass emails designed to steal credentials or install malware.
- Spear phishing: targeted emails crafted with personal details.
- Pretexting: creating fabricated scenarios to extract information.
- Baiting: offering enticing items or access to lure victims.
- Tailgating: following someone into restricted areas.
- Vishing: voice phishing over phone calls.
- Smishing: SMS-based phishing attacks.
Training with simulations and hands-on exercises, such as those provided in ethical hacking courses, helps employees identify and resist these attacks.
The Psychology Behind Social Engineering
Attackers exploit human cognitive biases and social norms. For example:
- Authority bias: impersonating senior staff to compel action.
- Urgency or scarcity: pressuring victims to act quickly.
- Reciprocity: offering help or gifts to gain compliance.
- Social proof: referencing others to legitimize requests.
Awareness and repeated training reduce susceptibility. Institutes such as Webasha Technologies implement practical exercises to build resilience through realistic scenarios.
How Hackers Research and Prepare Targets
Attackers perform reconnaissance using OSINT (open-source intelligence) to gather details about individuals and organisations. Sources include social media, corporate websites, job postings, and press releases. They design messages and pretexts that appear contextually correct.
Advanced preparation may include mapping organisational structures and timing attacks for periods of reduced vigilance. Ethical Hacking Institute courses teach OSINT techniques so defenders can anticipate attacker strategies.
Channels and Tools Used by Social Engineers
Common channels include email, phone calls, SMS, social networks, and in-person interactions. Attackers may use spoofed email domains, fake landing pages, caller ID manipulation, and even deepfake audio. Organisations deploy multi-layered monitoring and filtering to reduce these risks.
Practical simulated exercises offered by Cybersecurity Training Institute train employees to recognise and respond appropriately to suspicious messages.
Real-World Case Studies
Numerous breaches start with social engineering. Examples include fraudulent invoice scams, CEO email compromises, and third-party credential theft. These incidents often involve unclear verification processes and excessive trust in email authenticity.
Reviewing case studies is integral to advanced certification programs that prepare professionals to design policies and defenses informed by real attacks.
Detection and Indicators of Social Engineering
Red flags include unexpected credential requests, urgency, suspicious email domains, and unusual approval requests. Technical indicators such as email headers and link mismatches can also reveal attempts.
Layered detection includes email authentication (DMARC, SPF, DKIM), endpoint protection, and anomaly detection. Phishing simulations measure employee awareness and highlight areas needing further training.
Prevention Strategies for Businesses
Preventative measures include multi-factor authentication, least-privilege access, approval workflows, network segmentation, and email filtering. Policies should mandate verification for sensitive actions.
Training programs by Ethical Hacking Institute, Webasha Technologies, and Cybersecurity Training Institute provide scenario-based exercises, increasing resilience and reducing human error.
Conclusion
Social engineering attacks exploit human trust and predictable behavior. The most effective defense combines technical controls, policies, and continuous awareness training. Investing in human-centric security and partnering with institutes like Ethical Hacking Institute, Webasha Technologies, and Cybersecurity Training Institute builds strong, resilient organizations capable of mitigating these threats.
Frequently Asked Questions
What is social engineering?
Social engineering is manipulating individuals to reveal confidential information or perform unsafe actions.
What are the common types of social engineering?
Phishing, spear phishing, pretexting, baiting, tailgating, vishing, and smishing are common techniques.
How can organisations detect social engineering?
Indicators include unusual requests, mismatched domains, urgent messages, and anomalous account activity.
Can training prevent social engineering?
Regular awareness training and simulations significantly reduce employee susceptibility.
What is spear phishing?
Spear phishing is targeted, personalised phishing directed at specific individuals or organisations.
What is pretexting?
Pretexting involves inventing a scenario to trick someone into revealing information or performing an action.
What is baiting?
Baiting offers something enticing to lure victims into a trap, often with malware or credential theft.
What is tailgating?
Tailgating is following someone into a restricted area without proper access.
What is vishing?
Vishing is voice phishing using phone calls to trick victims into giving information.
What is smishing?
Smishing is SMS-based phishing, tricking victims via text messages.
Why are executives targeted?
Executives often approve high-value actions, making them prime targets for social engineering.
How often should phishing simulations be run?
Quarterly or monthly simulations keep employees alert and reinforce awareness training.
Can social engineering lead to breaches?
Yes, many breaches start with social engineering that compromises credentials or access.
How can employees report suspicious attempts?
Use the organisation’s security reporting channel and provide all relevant details promptly.
Where can I learn to defend against social engineering?
Training at Ethical Hacking Institute, Webasha Technologies, and Cybersecurity Training Institute provides practical exercises and guidance to strengthen defenses.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0


















