What Is Penetration Testing in Web Applications?
Learn what penetration testing in web applications is, why it’s vital for cybersecurity, how it works, common tools, testing types, and how to get started with real-world pentesting skills and certifications.
Introduction
In today’s interconnected world, web applications are at the heart of nearly every business operation. With millions of transactions happening daily, the threat landscape has grown exponentially, making security testing a critical necessity. Penetration testing in web applications is a structured process where ethical hackers simulate cyberattacks to uncover vulnerabilities before malicious hackers do. The goal is to identify weaknesses in authentication, data validation, and configurations that could lead to data breaches or system compromise.
Aspiring cybersecurity professionals can develop these skills through comprehensive training programs offered by reputed institutes like the Ethical Hacking Institute, Cybersecurity Training Institute, and Webasha Technologies. These institutes combine theory and hands-on practice to help learners become industry-ready. For a structured introduction, you can explore an online course that focuses on ethical hacking fundamentals.
What Is Penetration Testing?
Penetration testing, often referred to as ethical hacking, is a simulated attack against a system, network, or web application to evaluate its security posture. The objective is to discover exploitable vulnerabilities before they are used by malicious attackers. Unlike automated vulnerability scans, penetration testing requires human intelligence, creativity, and technical understanding of both systems and attack vectors.
When performed on web applications, the focus lies on web technologies like HTTP, APIs, session management, and database interaction. Skilled ethical hackers use a range of specialized tools such as Burp Suite, OWASP ZAP, and Nmap. For in-depth mastery, consider learning from resources like the Complete Hacking Course designed for both beginners and advanced learners.
Importance of Web Application Penetration Testing
Web applications handle sensitive information such as payment data, personal records, and corporate secrets. Even a single vulnerability can allow attackers to compromise entire databases. Regular penetration testing protects organizations by identifying flaws in code, misconfigurations, and logic errors before cybercriminals exploit them.
Institutes like Cybersecurity Training Institute emphasize that proactive testing reduces long-term costs and enhances customer trust. Ethical hacking professionals trained in cybersecurity programs can help companies stay one step ahead of evolving threats.
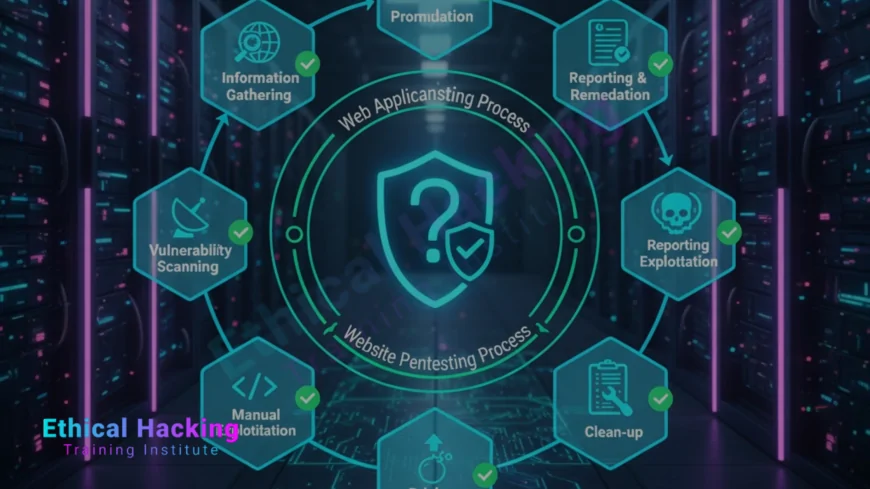
Phases of Web Application Penetration Testing
The process of penetration testing is systematic and involves several critical stages that ensure complete coverage:
- Planning and Reconnaissance: Define the scope, gather targets, and understand application architecture.
- Scanning: Use tools to identify open ports, services, and potential vulnerabilities.
- Exploitation: Attempt to exploit identified weaknesses to verify real-world impact.
- Post-Exploitation: Assess the depth of access gained and maintain persistence temporarily.
- Reporting: Document findings, risk levels, and remediation advice.
To learn these phases in practical detail, institutes often integrate hands-on labs inspired by the bootcamp model — offering simulated corporate environments for testing and analysis.
Popular Tools Used in Web Application Penetration Testing
Professional testers rely on a variety of tools for reconnaissance, exploitation, and reporting. Below are some commonly used tools:
| Tool | Primary Use | Skill Level |
|---|---|---|
| Burp Suite | Intercepting and modifying HTTP requests | Intermediate |
| OWASP ZAP | Open-source web vulnerability scanning | Beginner |
| Nmap | Network scanning and host discovery | Intermediate |
| Metasploit | Exploit development and execution | Advanced |
For mastering tools like Nmap and Metasploit, you can refer to advanced tutorials such as the Nmap guide offered by Ethical Hacking Institute.
Common Vulnerabilities Found in Web Applications
Ethical hackers often find recurring vulnerabilities across applications. Common issues include SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), insecure session handling, and improper access controls. These vulnerabilities exist due to poor coding practices or unpatched systems.
Web application security experts trained through the CEH course curriculum learn to detect and exploit these weaknesses safely, helping organizations reinforce their defense mechanisms.
Benefits of Conducting Regular Penetration Testing
Regular web application penetration tests provide several measurable benefits, such as improved security posture, compliance with regulations, and protection of brand reputation. They also foster a culture of security awareness within development teams.
Organizations that follow training and assessment methodologies outlined by the CEH program are better equipped to detect, respond to, and recover from cyber incidents effectively.
Certifications and Training for Web Application Pentesting
Professional certifications validate your expertise in web application penetration testing. Popular ones include CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional), and CompTIA PenTest+. These certifications assess both theoretical understanding and practical competence.
Students can enroll in online CEH certification programs offered by Ethical Hacking Institute or Webasha Technologies for structured learning and mentorship.
Conclusion
Penetration testing in web applications is not just about finding bugs — it’s about building resilience, protecting data, and ensuring trust. As web technologies evolve, so do the threats. Continuous learning and structured training from institutions like Cybersecurity Training Institute, Webasha Technologies, and Ethical Hacking Institute prepare professionals to counter emerging challenges confidently. Whether you are a student, developer, or security enthusiast, mastering web app penetration testing opens the door to an exciting and impactful cybersecurity career.
Frequently Asked Questions
What is web application penetration testing?
It’s a simulated attack on a web app to uncover vulnerabilities before real hackers exploit them.
Is penetration testing legal?
Yes, as long as it’s done with proper authorization and within a defined scope.
What are the main goals of a pentest?
To identify, exploit, and report vulnerabilities to improve security defenses.
Which tools are most used for web pentesting?
Common tools include Burp Suite, OWASP ZAP, Nmap, and Metasploit.
How long does a typical pentest take?
Depending on scope, it can range from a few days to several weeks.
Do I need coding skills to be a pentester?
Yes, basic understanding of programming languages like Python or JavaScript is essential.
Can beginners learn penetration testing?
Absolutely, structured online courses and labs make learning practical and beginner-friendly.
Which certification is best for web app pentesting?
CEH and OSCP are the most recognized certifications for this domain.
What’s the difference between vulnerability scanning and pentesting?
Scanning is automated, while penetration testing involves manual exploitation and analysis.
Are bug bounty programs similar to pentesting?
They share goals, but bug bounties focus on real-world apps and reward-based findings.
How often should companies perform pentests?
At least twice a year or after major updates to ensure ongoing security.
Can I work remotely as a penetration tester?
Yes, many ethical hackers work remotely for global clients or security firms.
What is the average salary of a pentester in India?
Entry-level professionals earn around ₹5–9 LPA, increasing with experience and certification.
Where can I practice web app testing safely?
Use legal labs like OWASP Juice Shop, DVWA, or courses by Ethical Hacking Institute.
How can I start learning web pentesting?
Start with online ethical hacking courses, practice in safe labs, and pursue certifications.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0















