What Is Penetration Testing and How Is It Done?
Penetration testing (pentesting) simulates cyberattacks to find vulnerabilities before hackers do. Learn the 5 phases, tools, types, real examples, and how to start as a beginner.
Introduction
Imagine hiring a professional thief to break into your house—then fix the locks before real criminals arrive. That’s penetration testing in cybersecurity.
Penetration testing (or pentesting) is a controlled, authorized cyberattack on your own systems. The goal? Find and fix weaknesses before malicious hackers exploit them.
Every major company—from banks to startups—relies on pentesting. In 2025, with AI-powered attacks rising, it’s more critical than ever. This guide walks you through what pentesting is, how it’s done step by step, and how even beginners can understand (or start) the process.
What Is Penetration Testing?
Pentesting simulates real-world attacks to evaluate security.
Key Goals
- Identify exploitable vulnerabilities
- Test security controls (firewalls, IDS, etc.)
- Measure potential business impact
- Provide actionable remediation
Pentest vs Vulnerability Scan
| Aspect | Vulnerability Scan | Penetration Test |
|---|---|---|
| Automation | Fully automated | Manual + automated |
| Depth | Surface-level | Exploitation & chaining |
| False Positives | High | Low (human verified) |
| Cost | $500–$5,000/year | $10,000–$100,000+ |
Types of Penetration Testing
Different targets require different approaches.
1. Network Penetration Testing
Tests servers, firewalls, and infrastructure.
- External: From the internet
- Internal: From inside the network
2. Web Application Testing
Focuses on websites and APIs.
- SQL injection, XSS, CSRF
- OWASP Top 10 coverage
3. Mobile App Testing
iOS/Android apps and backend.
4. Cloud Pentesting
AWS, Azure, GCP configurations.
5. Physical Pentesting
Access controls, locks, cameras.
6. Social Engineering
Phishing, vishing, pretexting.
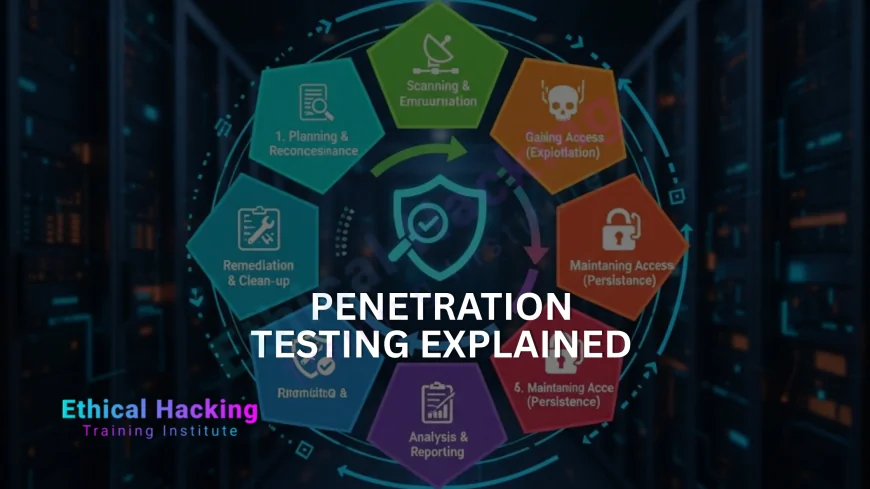
The 5 Phases of Penetration Testing
Every pentest follows this structured methodology.
Phase 1: Planning and Reconnaissance
Define scope, goals, and gather intel.
- Get written authorization (Rules of Engagement)
- Passive recon: WHOIS, Shodan, Google dorking
- Active recon: DNS enumeration, subdomain discovery
Phase 2: Scanning
Map the attack surface.
- Port scanning with Nmap
- Vulnerability scanning (Nessus, OpenVAS)
- Web crawling (Burp Spider, ZAP)
Mastering Nmap is essential in this phase for accurate network mapping.
Phase 3: Gaining Access
Exploit vulnerabilities to breach systems.
- Exploit public vulnerabilities (CVEs)
- Password cracking (Hashcat, John)
- Web exploits (SQLi, file inclusion)
- Use Metasploit for automated exploitation
Phase 4: Maintaining Access
Establish persistence like real attackers.
- Install backdoors
- Create rogue accounts
- Tunnel traffic (SSH, Meterpreter)
Phase 5: Analysis and Reporting
Document findings and recommend fixes.
- Risk rating (CVSS scores)
- Proof of concept (screenshots, logs)
- Executive summary + technical details
- Remediation roadmap
Essential Pentesting Tools (Beginner-Friendly)
All pre-installed in Kali Linux.
Recon Tools
- theHarvester: Email/OSINT gathering
- Maltego: Visual link analysis
- Amass: Subdomain enumeration
Scanning Tools
- Nmap: Network discovery
- Nessus/OpenVAS: Vulnerability scanning
Exploitation Tools
- Metasploit: Exploit framework
- SQLMap: Automated SQL injection
- Burp Suite: Web proxy/interception
Post-Exploitation
- Meterpreter: Advanced payload
- Empire: C2 framework
- Mimikatz: Credential dumping
Real-World Pentest Example
Target: E-commerce website
Findings:
- SQL injection in login form → database dump
- Outdated WordPress plugin → remote code execution
- Weak admin password → full server access
Impact: Full customer data breach possible
Fixes: Input sanitization, patch plugins, enforce MFA
Black, White, and Gray Box Testing
Black Box
No prior knowledge. Simulates external hacker.
- Longest duration
- Most realistic
White Box
Full access to source code, architecture.
- Fastest, most thorough
- Best for web apps
Gray Box
Limited credentials (e.g., user account).
- Balanced approach
- Most common in practice
How to Get Started with Pentesting (Beginners)
Step 1: Learn Prerequisites
- Linux command line
- Basic networking (TCP/IP, HTTP)
- Web technologies (HTML, SQL)
Step 2: Set Up Your Lab
- Install Kali Linux (VM)
- Download vulnerable machines:
- Metasploitable
- DVWA
- Juice Shop
Step 3: Practice Legally
- TryHackMe (guided rooms)
- HackTheBox (realistic machines)
- PortSwigger Web Academy (free)
Step 4: Get Certified
- eJPT → CEH → OSCP
Many beginners accelerate with an intensive pentesting bootcamp that includes live labs and mentorship.
Legal and Ethical Considerations
- Always get written permission
- Never test systems you don’t own
- Follow scope strictly
- Destroy all data post-test
Conclusion: Pentesting Is Prevention in Action
Penetration testing isn’t about breaking things—it’s about making them unbreakable. By simulating real attacks, you discover weaknesses while they’re still fixable, not after a breach costs millions.
Every modern organization needs regular pentesting. Whether you’re a business owner protecting customers or an aspiring ethical hacker, understanding the process is step one.
Start today: spin up a vulnerable VM, run your first Nmap scan, and see security from the attacker’s perspective. The best defense begins with knowing how to attack. For structured learning, explore online CEH programs with hands-on pentesting modules.
Frequently Asked Questions
How long does a pentest take?
1–4 weeks depending on scope. Web apps: 3–7 days. Full enterprise: 2–4 weeks.
How much does pentesting cost?
$5,000–$50,000+ based on size. Small web app: $5K. Large network: $30K+.
Is pentesting legal?
Yes, with written authorization. Without permission, it’s hacking.
Can I pentest my own systems?
Yes! Set up isolated labs with vulnerable VMs. Never test production without planning.
What’s the hardest part of pentesting?
Reporting. Technical findings must translate to business risk and fixes.
Do I need coding for pentesting?
Not required, but Python/Bash helps automate tasks and write exploits.
Black box vs white box: which is better?
Both. Black box = realistic. White box = thorough. Most use gray box.
What’s a “zero-day” in pentesting?
A vulnerability unknown to the vendor. Rare in standard tests.
Can automated tools replace pentesters?
No. Tools find known issues. Humans chain exploits creatively.
How often should pentesting be done?
Annually minimum. After major changes, quarterly for high-risk systems.
Is OSCP worth it?
Yes. Gold standard for hands-on pentesting skills.
Can pentesting find all vulnerabilities?
No. It’s a snapshot. Combine with scanning, monitoring, and bug bounties.
What’s post-exploitation?
Actions after initial breach: privilege escalation, data exfil, persistence.
Do pentesters get hacked?
Rarely. They use isolated VMs and follow strict opsec.
Best first tool to learn?
Nmap. Universal for network discovery and service enumeration.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0

















