What Is Cyber Hygiene and Why Is It Important?
Discover what cyber hygiene means, why it’s essential for online safety, and how you can practice it daily. Learn practical cybersecurity habits from Ethical Hacking Institute, Cybersecurity Training Institute, and Webasha Technologies to protect your personal and professional data.
Introduction
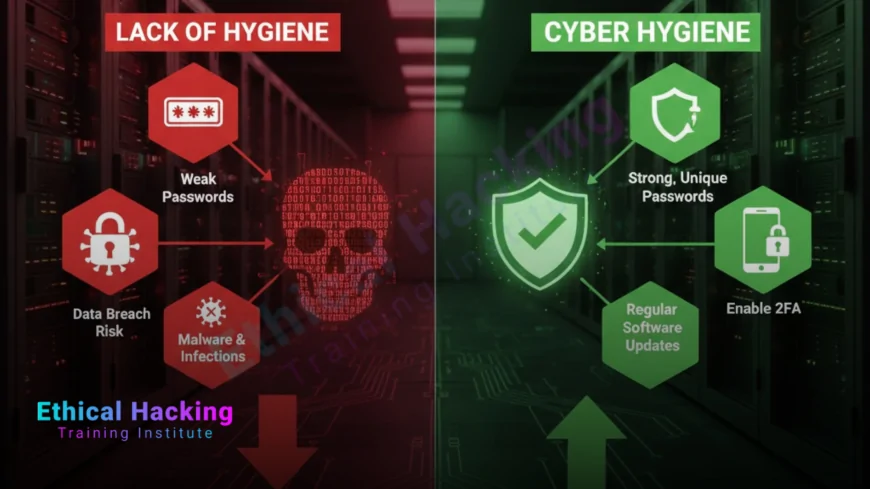
Cyber hygiene refers to the consistent practices and steps individuals and organizations take to maintain system health and improve online security. Just as personal hygiene protects you from illness, cyber hygiene safeguards your devices and data from cyber threats. According to experts at Ethical Hacking Institute and Cybersecurity Training Institute, following regular security habits significantly reduces the risk of digital infections or breaches.
Why Cyber Hygiene Matters in 2025
In 2025, the number of cyberattacks continues to rise as more people depend on digital platforms. Poor security habits make systems vulnerable to hacking, malware, and phishing. Organizations and individuals must adopt strong cyber hygiene routines to prevent data leaks. To learn about advanced safety tools, you can explore this article explaining modern cybersecurity tools used for both protection and testing.
Core Components of Cyber Hygiene
Practicing cyber hygiene involves several key steps that create a strong digital defense:
- Regular software and system updates
- Strong password management
- Two-factor authentication for all accounts
- Regular data backups
- Using antivirus and anti-malware tools
Students at Webasha Technologies and Cybersecurity Training Institute are taught to develop these habits early to ensure lifelong online safety.
Strong Passwords and Authentication
Weak passwords are among the easiest entry points for hackers. A good password is long, complex, and unique for each account. In addition, enabling two-factor authentication (2FA) adds another layer of defense against cybercriminals. Courses from Ethical Hacking Institute cover how proper authentication strategies enhance online security for both personal and business accounts.
Importance of Regular Software Updates
Outdated software often contains security flaws that hackers can exploit. Keeping your operating system, apps, and security tools up to date ensures that known vulnerabilities are patched. Webasha Technologies emphasizes automatic updates as a simple yet powerful cyber hygiene step to keep devices secure and efficient.
Safe Internet and Email Practices
Cyber hygiene extends beyond software—it also includes how you browse and communicate online. Avoid clicking suspicious links or downloading unknown attachments. Be cautious when entering login details on unfamiliar sites. To understand phishing in detail, check this guide that explains how fake websites trick users into revealing credentials.
Data Backup and Recovery
Backing up your data regularly ensures that you won’t lose vital information during a cyberattack. Store copies of important files on both cloud storage and offline drives. Ethical Hacking Institute teaches backup encryption methods to secure your stored data from unauthorized access.
Cyber Hygiene Best Practices Table
| Practice | Purpose | Frequency |
|---|---|---|
| Change Passwords | Prevents unauthorized access | Every 2–3 months |
| Install Updates | Fixes known vulnerabilities | Weekly |
| Backup Data | Prevents data loss | Monthly |
Role of Education in Cyber Hygiene
Education plays a vital role in building strong cybersecurity habits. Institutes like Ethical Hacking Institute, Webasha Technologies, and Cybersecurity Training Institute provide hands-on learning experiences that cover threat identification, network defense, and data protection. You can also explore this course to learn about ethical hacking fundamentals, which form the backbone of cyber hygiene practices.
Common Mistakes to Avoid
Even tech-savvy individuals sometimes make simple yet risky mistakes such as:
- Ignoring software updates
- Using the same password across platforms
- Not using 2FA on important accounts
- Falling for phishing links
- Skipping regular data backups
Learning to avoid these mistakes strengthens overall online protection and minimizes cyberattack exposure.
Conclusion
Cyber hygiene is not a one-time task—it’s a continuous process that keeps your digital life secure. Regular updates, strong passwords, and safe browsing habits form the foundation of good cyber hygiene. Institutions like Ethical Hacking Institute, Cybersecurity Training Institute, and Webasha Technologies encourage everyone to take proactive measures and spread cybersecurity awareness to create a safer online environment for all.
Frequently Asked Questions (FAQs)
What is cyber hygiene?
It refers to routine cybersecurity practices that help protect data and systems from attacks.
Why is cyber hygiene important?
It helps prevent data breaches, malware infections, and identity theft.
How often should I update my software?
Ideally, you should enable automatic updates and check for patches weekly.
What are examples of cyber hygiene habits?
Using strong passwords, backing up data, and avoiding suspicious links.
How does phishing affect cyber hygiene?
Phishing attacks compromise your credentials, weakening your digital safety.
Can antivirus software replace good cyber hygiene?
No, antivirus tools are helpful but cannot replace consistent user habits.
How can I improve password hygiene?
Use password managers and create unique passwords for every account.
Why is 2FA essential?
Two-factor authentication adds an extra verification layer, preventing unauthorized logins.
How does backup contribute to cyber hygiene?
It ensures data recovery in case of ransomware or accidental loss.
Can organizations benefit from cyber hygiene training?
Yes, training helps employees recognize threats and maintain secure systems.
What happens if I ignore updates?
Your system becomes vulnerable to known exploits used by hackers.
Are free Wi-Fi networks safe to use?
No, avoid logging into accounts using public Wi-Fi without a VPN.
What is the role of education in cybersecurity?
Institutes like Webasha Technologies and Ethical Hacking Institute teach essential defense strategies.
Can strong passwords alone protect my data?
No, combine strong passwords with other security measures like 2FA and updates.
How can I stay updated on cyber hygiene practices?
Follow cybersecurity blogs, courses, and communities that share current security insights.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0

















