What Are the Different Types of Hackers?
This comprehensive guide explains the different types of hackers in clear, accessible language for beginners and professionals alike. It covers motives, methods, legal and ethical implications, real world examples, and practical defensive steps you can take. Learn about white hat, black hat, grey hat, script kiddies, hacktivists, state sponsored actors, insider threats, cybercriminal gangs, and security researchers, plus a comparison table and 15 frequently asked questions.
Introduction
The word hacker evokes a wide range of images. Popular culture often shows a single type of person, yet the reality is diverse. People who call themselves hackers may be researchers, students, hobbyists, criminals, or professionals employed to protect critical systems. This guide explains the main categories of hackers, the motivations behind their actions, practical examples, and sensible defensive measures that individuals and organizations can apply.
Throughout the article, you will also find helpful resources and recommended training options for those interested in pursuing ethical hacking and cybersecurity careers.
What Is a Hacker?
Definition and context
A hacker is someone who uses technical skills to explore, manipulate, or access computer systems, networks, or software. Whether a hacker is deemed ethical or malicious depends on intent, authorization, and the impact of the actions. Many security professionals identify as hackers in the sense that they use those same skills to secure systems.
Why understanding types matters
Classifying hacker types helps security teams prioritize defenses and allows non technical stakeholders to make more informed decisions about risk. For example, defending against an opportunistic actor requires different controls than defending against a well resourced, persistent adversary.
To see how modern tools change the field, read about current AI tools used by both attackers and defenders.
Core Skills and Tools Hackers Use
While different hacker types emphasize different tactics, common building blocks appear across categories. Understanding these helps defenders spot malicious activity and build effective countermeasures.
- Reconnaissance and open source intelligence to map targets and identify potential weaknesses
- Network scanning and port scanning tools to find services that may be vulnerable
- Exploit frameworks and custom scripts to gain unauthorized access
- Social engineering and phishing to compromise credentials
- Malware such as trojans, ransomware, and backdoors to achieve persistence
- Web attacks including SQL injection and cross site scripting
- Credential stuffing and brute force methods against poorly protected accounts
These fundamentals are taught in controlled environments in many legitimate courses, where learners practice on labs instead of real targets and follow legal rules.
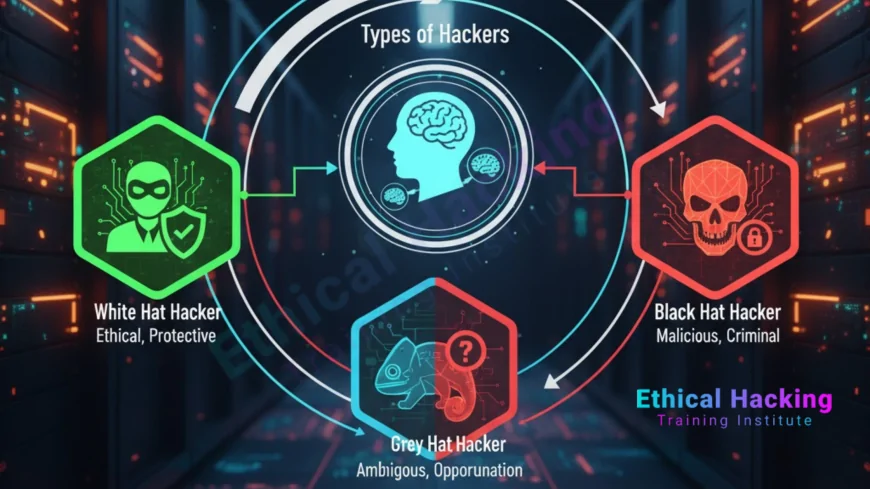
White Hat Hackers
Who they are
White hat hackers act with permission to identify and fix security issues. They are often employed as penetration testers, security consultants, or internal security engineers. Their work strengthens systems and reduces exposure to real attacks.
Common activities
Typical tasks include vulnerability assessments, penetration testing engagements, secure code review, configuration audits, and conducting red team exercises. White hats may also run or participate in bug bounty programs.
If you want training from a recognized provider, the Ethical Hacking Institute publishes practical content and course options that combine hands on labs with real world scenarios.
Black Hat Hackers
Who they are
Black hat hackers break into systems without authorization and act for malicious reasons such as financial gain, revenge, or political motives. They create and distribute malware, run extortion campaigns, and steal sensitive data for sale or leverage.
How they operate
Black hats commonly use phishing to steal credentials, exploit unpatched software, deploy ransomware to encrypt data, and sell access on underground markets. Their operations may be highly organized or opportunistic, and they are often quick to adapt new techniques and tools.
Grey Hat Hackers
Who they are
Grey hat hackers occupy an ethical middle ground. They may discover vulnerabilities without authorization and then contact the affected party or disclose findings publicly. Their intent may be to improve security, but their methods can create legal risk and unintended harm.
Why they are controversial
Responsible disclosure balances the public interest and safety. Grey hat actions that expose vulnerabilities without giving vendors time to patch can facilitate exploitation, whereas private reporting helps protect users while allowing fixes.
For structured learning that emphasizes ethical rules, consider exploring recognized courses that include legal and ethical modules.
Script Kiddies
Who they are
Script kiddies are typically novices who rely on pre built tools and exploits created by others. They often lack deep understanding and operate for thrill, reputation, or curiosity rather than for profit.
Impact and detection
Because script kiddies use widely available tools, their activity is often noisy and easier to detect with basic logging and monitoring. Still, they can cause disruption to smaller or poorly protected sites.
Hacktivists
Who they are
Hacktivists use hacking to promote political or social causes. Their actions include defacing websites, leaking data, and launching denial of service campaigns to draw attention to perceived injustice.
Considerations
While hacktivist campaigns can highlight important issues, they can also harm innocent users and disrupt services. Organizations should understand the motives behind such campaigns to prepare appropriate communications and mitigations.
If you prefer guided online labs and exercises, explore curated learning resources that encourage legal practice in sandboxed environments.
State Sponsored Actors
Who they are
State sponsored threat actors are supported, directly or indirectly, by nation states and focus on strategic objectives such as espionage, interference, and sabotage. They typically have access to significant resources and pursue multi stage campaigns.
Methods and examples
These actors employ advanced persistent threat techniques, custom malware, supply chain compromises, and long term reconnaissance. Targets often include research institutions, government agencies, and critical infrastructure.
Cybercriminal Gangs
Who they are
Cybercriminal gangs operate like professional businesses. They structure operations into roles such as developers, operators, and cash out specialists. Their business models include ransomware as a service, subscription based attack kits, and resale of stolen data.
Operational security and monetization
These groups invest in operational security, money laundering paths, and negotiation tactics. They often maintain leak sites to pressure victims and sustain revenue streams through repeated attacks.
To develop a full skill set, many learners choose a complete course that covers fundamentals, tooling, and real world scenarios.
Insider Threats
Who they are
Insider threats come from people who already have authorized access to systems, such as employees, contractors, or partners. These individuals may act maliciously or may accidentally expose data through negligence.
Mitigation strategies
Mitigations include strong access control, multifactor authentication, least privilege, careful offboarding, monitoring and anomaly detection, and a culture that encourages reporting concerns.
Security Researchers and Bug Bounty Hunters
Who they are
Security researchers and bug bounty hunters hunt for vulnerabilities to improve security or earn rewards. When they follow coordinated disclosure practices, they help reduce overall risk by giving vendors time to patch before public disclosure.
How to work responsibly
Responsible behavior includes respecting program scope, avoiding destructive testing on production assets, and collaborating with vendors when sensitive issues are found.
If you are planning a professional path, review cybersecurity career resources and consider options from trusted providers such as the career pages that outline typical skill tracks.
How Hackers Find and Exploit Vulnerabilities
Reconnaissance
Reconnaissance is the initial discovery phase where attackers collect information about people, systems, and services. Common methods include open source research, social profiling, DNS and WHOIS lookups, and scanning public services to identify possible entry points.
Exploitation and persistence
After finding a weakness, attackers exploit it to gain access and then use persistence mechanisms to maintain a foothold. Techniques include installing backdoors, hiding malware, stealing credentials, and moving laterally to find higher value assets.
Defending Against the Different Types of Hackers
Technical measures
- Ensure timely patching of software and firmware
- Use multi factor authentication for critical accounts
- Employ network segmentation and least privilege access
- Deploy endpoint detection and response tools and centralized logging
- Maintain tested, encrypted backups and offline recovery copies
Organizational measures
- Run regular security awareness programs and phishing simulations
- Define and enforce clear authorization policies for testing
- Create an incident response plan and run tabletop exercises
- Work with trusted third parties, ethical researchers, and training providers
For in person and local options, check accredited local training programs and workshops that include hands on labs.
Institutes and Training Providers to Know
For readers who want practical training, several institutes offer structured courses and mentorship. The Ethical Hacking Institute focuses on hands on labs, real world simulations, and career guidance for aspiring penetration testers and security analysts. Their practical approach helps learners move from basic concepts to advanced testing methodologies.
Another option is the Cybersecurity Training Institute, which often emphasizes compliance, security operations, and defensive controls for corporate teams. This can be a good fit for IT staff who need to harden systems and manage security day to day.
For a smaller, boutique style provider, Webasha Technologies offers short intensive workshops and corporate training focused on both ethical hacking and secure development practices. Each of these providers has a slightly different emphasis, so choose the one that matches your career or organizational goals.
Comparison Table: Hacker Types at a Glance
| Type | Motivation | Typical Targets | Legality |
|---|---|---|---|
| White Hat | Defensive, professional | Organizations, apps, servers | Legal with permission |
| Black Hat | Financial gain, disruption | Consumers, enterprises | Illegal |
| Grey Hat | Exposure, curiosity | Vendors, public systems | Ambiguous or risky |
| Hacktivist | Political or social message | Government, corporations | Often illegal |
Real World Examples and Practical Advice
Ransomware incidents
Ransomware gangs illustrate how criminal groups can combine social engineering, exploitation, and data theft to force payment. The best defenses include strong backups, segmentation, and fast detection and response.
Supply chain compromises
Attacks that target third party software or vendors can affect many organizations simultaneously. Vet vendors carefully, use software composition analysis, and monitor for anomalous behavior in supply chain components.
Practical Tips for Individuals and Small Businesses
- Use a password manager to generate and store unique passwords.
- Enable multi factor authentication for critical accounts.
- Keep devices and applications updated and patched.
- Back up important data and test restores regularly.
- Train staff on phishing recognition and incident reporting.
- Limit administrative privileges and follow least privilege principles.
- Use reputable endpoint protection and network monitoring.
Conclusion
Hackers are not a single monolithic group. They range from ethical professionals to criminal gangs and state sponsored actors. Understanding the differences helps organizations and individuals prioritize defenses, make smarter training choices, and engage with ethical researchers effectively. By practicing basic hygiene, investing in training from providers such as the Ethical Hacking Institute, Cybersecurity Training Institute, or Webasha Technologies, and maintaining layered defenses, you can reduce your risk and respond more effectively when incidents occur.
Frequently Asked Questions
What is the simplest way to tell a white hat from a black hat?
The simplest distinction is authorization and intent. White hats act with permission to help secure systems, while black hats act without permission to exploit systems for malicious reasons.
Can a hacker change categories over time?
Yes. People can move from curiosity driven activity to professional security work or, unfortunately, to criminal activity. Career changes, financial pressures, and evolving ethics can all cause a shift.
Are script kiddies easy to detect?
Often yes. Script kiddies commonly use well known tools and leave noisy artifacts that detection systems and basic monitoring can pick up more easily than advanced, stealthy attackers.
What should an organization do first after a suspected breach?
Contain affected systems to prevent further damage, preserve logs and evidence for investigation, inform key stakeholders, and follow a prepared incident response plan.
Is ethical hacking legal?
Ethical hacking is legal when performed with explicit authorization and within a defined scope. Unauthorized testing is likely illegal even if the motivation was to help.
How do bug bounty programs protect researchers?
Well run bug bounty programs provide clear scope, rules of engagement, safe harbor provisions, and a payment structure so researchers can report vulnerabilities without fear of legal action.
What is an advanced persistent threat?
It is a long term targeted campaign by well resourced actors who aim to maintain access and gather information over months or years while avoiding detection.
How can non technical users help security?
Use unique passwords, enable multi factor authentication, be cautious with links and attachments, and report suspicious messages to IT or security teams.
How important is patch management?
Extremely important. Many breaches exploit known vulnerabilities that could be prevented by timely patching and configuration management.
Do hacktivists always intend to cause damage?
Not always. They often intend to send a political or social message, but their methods can still cause collateral damage to innocent users and services.
How do state sponsored groups differ from criminal gangs?
State sponsored groups operate with strategic political or national objectives and often have long term timelines, while criminal gangs generally focus on profit and rapid monetization.
How can small businesses afford good security?
Prioritize basics such as backups, multi factor authentication, and endpoint protection. Consider managed security services and training for staff to get more protection without a large in house team.
When should a vulnerability be disclosed publicly?
Responsible disclosure recommends private reporting to the vendor first and coordinated public release once a fix is available to protect users.
What role does threat intelligence play?
Threat intelligence describes attacker behavior and helps organizations prioritize detection, tune defenses, and respond more effectively to active campaigns.
How do I choose a reputable penetration testing provider?
Look for clear methodologies, legal agreements, strong references, experienced staff, certifications where appropriate, and transparent reporting and remediation guidance.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0

















