How to Start a Career in Ethical Hacking After Graduation?
A practical roadmap for graduates who want to become ethical hackers: essential skills, certifications, lab setups, bug bounty and CTF practice, building a portfolio, finding entry-level roles, and long-term career tips. Learn how to convert curiosity into a paid cybersecurity career.
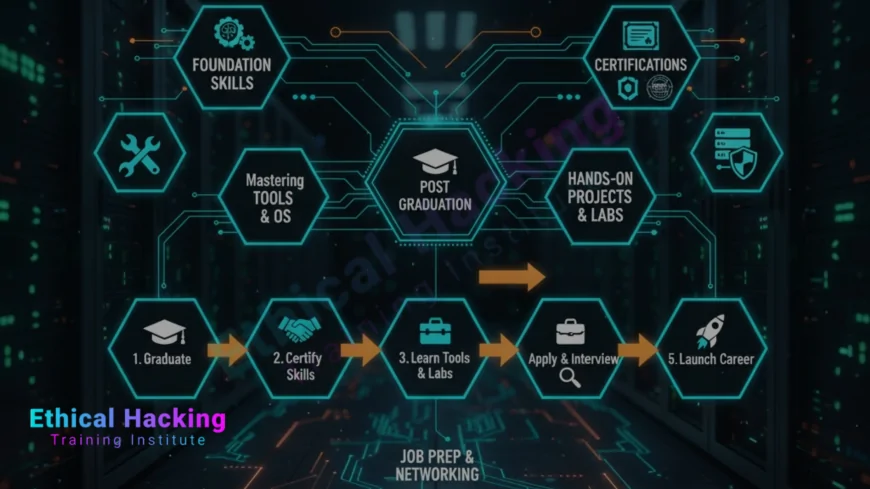
Introduction
Graduating with an interest in cybersecurity is an excellent starting point for a career in ethical hacking. The field rewards curiosity, persistence, and hands-on practice. This guide walks you from the first steps after graduation through building a marketable skillset, getting certified, gaining experience in real labs and bug bounty programs, and landing your first job in the industry.
Understanding Ethical Hacking
Ethical hacking is authorised and lawful testing of systems to discover and fix vulnerabilities before malicious actors exploit them. Ethical hackers use similar tools and methodologies as attackers, but they follow rules of engagement and focus on improving security. To learn the craft, many graduates combine structured courses with independent lab practice so theory and practice reinforce each other.
Essential Technical Foundations
Before diving into offensive tools, build a solid foundation: networking (TCP/IP, DNS, routing), operating systems (Linux and Windows internals), web technologies (HTTP, HTML, JavaScript), and basic scripting (Python or Bash). These fundamentals let you understand why vulnerabilities exist and how attackers chain them. Supplement your study with guided training that includes both explanations and hands-on exercises.
Practical Tools You Should Master
Familiarity with the core toolset is essential: Nmap for discovery, Burp Suite for web testing, Wireshark for packet analysis, Metasploit for exploitation, and grep/awk/jq for data handling. Learn to automate repetitive tasks with scripts so you can focus on analysis. A focused module on Nmap helps you perform fast and accurate reconnaissance.
Certifications That Boost Credibility
Certifications validate knowledge and can speed up hiring. Useful early certs include CompTIA Security+ and CEH for broad knowledge, while OSCP is highly respected for hands-on penetration testing skills. If you’re preparing for vendor or exam-focused pathways, follow a clear certification plan that balances study and lab time.
Build a Home Lab and Safe Practice Environment
A home lab gives you a legal place to experiment. Set up virtual machines with VirtualBox or VMware, deploy intentionally vulnerable targets like OWASP Juice Shop or Metasploitable, and practice end-to-end engagements. Use snapshots to recover quickly and keep the lab isolated from production networks. Completing hands-on practical exercises prepares you for real-world testing.
Participate in CTFs and Bug Bounty Programs
Capture The Flag (CTF) competitions and bug bounty platforms are the fastest ways to sharpen skills. CTFs train problem solving across web, crypto, and binary categories, while bug bounties teach you to write professional reports and interact with triage teams. Start on beginner-friendly platforms, then progress to more competitive environments as your skills mature. Many graduates convert CTF wins and bounty writeups into portfolio pieces to show employers and recruiters who value demonstrable bootcamp experience.
Build a Professional Portfolio
Employers want evidence of practical ability. Maintain a GitHub with scripts and write-ups, a blog with clear methodology, and redacted samples of penetration test reports or bug bounty disclosures. Document lab setups, steps to reproduce (PoC), and remediation advice. A concise portfolio often outweighs an unproven resume because it demonstrates problem-solving and communication skills honed through structured certification and projects.
Networking and Community Involvement
Join local and online security communities: meetups, Discord servers, Reddit forums, and professional groups. Volunteer for open-source security projects or local non-profits that need vulnerability assessments; these experiences create references and real-world stories for interviews. Also consider attending events and conferences to meet hiring managers and peers who can introduce you to job opportunities or mentorship pathways described in many institute guides.
How to Apply for Entry-Level Roles
Start with roles that build context: SOC analyst, junior security analyst, or security operations intern. These positions expose you to incident handling, logging, and enterprise tooling. When applying, tailor your resume to highlight hands-on labs, CTF achievements, certifications, and specific tools used. Customise cover letters for each role and include a link to your portfolio or GitHub demonstrating real work and class projects.
Internships, Apprenticeships and Mentorship
Internships provide supervised exposure to real systems and reporting practices. Apprenticeships and mentorship programs help you learn industry standards and report-writing etiquette. Reach out to alumni from training institutes and ask for short mentorship calls; experienced practitioners often give useful feedback on your methodology and reports learned through structured online study.
Soft Skills and Professionalism
Ethical hackers need clear communication and professional behaviour. Learn to write executive summaries for non-technical stakeholders, explain risk in business terms, and be punctual with deliverables. Honesty, legal compliance, and respect for client boundaries are essential; a polished report and calm communication during an incident often make as much impact as the technical findings acquired through focused program experiences.
Table: Roadmap at a Glance
| Stage | Focus | Outcome |
|---|---|---|
| Fundamentals | Networking, OS, scripting | Core understanding |
| Hands-on | Home lab, tools practice | Reproducible skills |
| Validation | Certifications & CTFs | Credibility |
| Experience | Internships, SOC roles | Professional practice |
Common Early-Career Mistakes to Avoid
Avoid these pitfalls: relying solely on theory, skipping write-ups, ignoring legal boundaries, and using cracked or pirated tools. Focus on reproducible methodology, clear documentation, and ethical behaviour. Do not share sensitive PoC details publicly without permission; instead, maintain redacted evidence in your private portfolio while showcasing methodology and remediation suggestions learned from real resources.
Long-Term Career Growth and Specialisations
As you gain experience, consider specialisations: web application pentesting, cloud security, IoT security, reverse engineering, or red teaming. Each path requires deeper study and different toolsets. Continuous certification and conference participation keep skills current and open doors to senior roles, consultancy, or leadership in security programmes; many professionals follow a structured mix of hands-on labs and advanced courses to move up.
How Employers Evaluate Junior Ethical Hackers
Employers look for practical signs: reproducible reports, lab projects, CTF results, and clear communication. They value curiosity, problem solving, and evidence that you can learn on the job. Demonstrating initiative—publishing writeups, sharing open-source tools, or contributing to security communities—gives you an edge during interviews and technical assessments, often more than an unproven degree alone.
Conclusion
Starting a career in ethical hacking after graduation is entirely achievable with discipline and a practical approach. Build strong technical foundations, practise in safe labs, earn respected certifications, participate in CTFs and bug bounties, and assemble a portfolio that proves your skills. Engage with the community, seek internships, and always act ethically. Institutes and bootcamps can accelerate learning but the most important ingredients are hands-on practice and consistent learning.
Frequently Asked Questions
Do I need a degree to become an ethical hacker?
No. Practical skills, certifications, and a strong portfolio are often more important than a degree in landing entry-level roles.
Which certification should I pursue first?
For beginners, consider CEH or CompTIA Security+. For hands-on credibility, OSCP is highly respected though more challenging.
How long does it take to become job-ready?
With focused study and practice, many graduates reach entry-level readiness in 6–12 months; timelines vary by prior experience and study intensity.
What is the best way to practice legally?
Use intentionally vulnerable labs, CTF platforms, and authorised bug bounty programs. Never test live systems without explicit permission.
Can bug bounties replace a full-time job?
Some hunters earn substantial income from bounties, but it is unpredictable; many combine bug bounties with freelance or full-time work for stability.
How important are soft skills?
Very important. Clear writing, communication, and the ability to explain technical issues to non-technical stakeholders are highly valued.
Should I specialise early or stay broad?
Start broad to build a foundation, then specialise in areas you enjoy and where demand is strong, such as cloud or web app security.
Are internships worth pursuing?
Yes. Internships give supervised, real-world experience that accelerates learning and improves employability.
How do I stand out in interviews?
Bring a portfolio with real writeups, show your lab environment, and be prepared to explain your thought process through past exercises.
What are good starter projects for my portfolio?
CTF solutions, vulnerable-app walkthroughs, small open-source security tools, and redacted pentest reports are excellent starter projects.
How much do entry-level ethical hackers earn?
Salaries vary by region. In India, entry-level roles often start around ₹4–8 LPA, rising with experience and certifications.
How do I keep my skills up to date?
Regular lab practice, following security blogs, participating in CTFs, and taking advanced courses keep skills current.
Can I learn ethical hacking remotely?
Yes. Many high-quality programs and labs are available online, allowing remote learners to get hands-on experience.
What ethical rules should I follow?
Always obtain written permission before testing, respect disclosure policies, avoid data exfiltration beyond what’s necessary for proof, and follow legal and client guidelines.
Where can I find mentorship as a new graduate?
Join local meetups, online communities, alumni networks, and reach out to instructors or practitioners who offer mentorship or office hours.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0















