How to Become a Freelance Ethical Hacker?
Want to become a freelance ethical hacker? This practical guide walks you through the exact steps: skills to learn, certifications to earn, lab setup, client acquisition, tools, pricing, legal considerations, and how to build a sustainable freelance cybersecurity business.
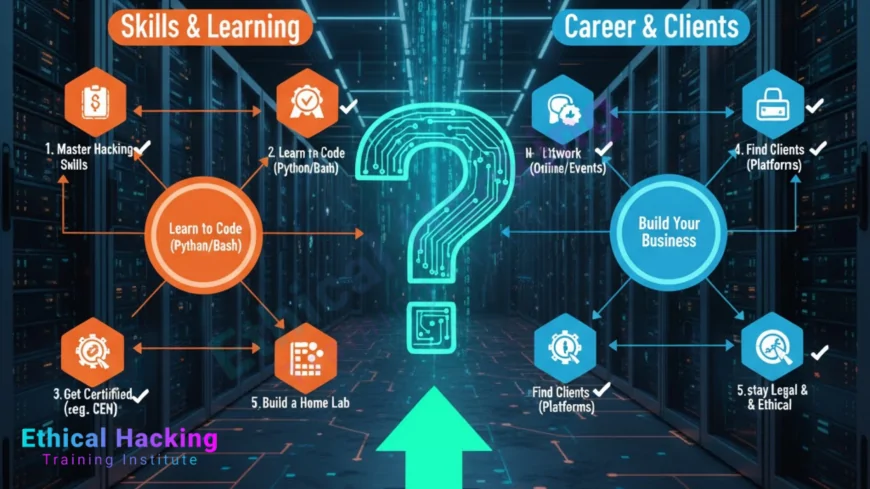
Introduction
Freelancing as an ethical hacker is a compelling way to turn security skills into income while enjoying flexibility. Freelance ethical hackers help organisations discover vulnerabilities, run penetration tests, participate in bug bounty programs, and provide remediation guidance. This guide will give you a clear, practical roadmap from the first skills to landing your first paid client and running a professional freelance security practice.
Why Choose Freelance Ethical Hacking?
Freelance ethical hacking appeals to many because it combines technical challenge, autonomy, and the potential for high earnings. You can choose short engagements like bug bounty submissions or longer pentest contracts. Freelancing allows you to pick clients, specialise in niches such as web applications or cloud security, and scale up as you gain reputation. Many learners complement practical work with structured training and mentorship from institutions like Ethical Hacking Institute to shorten the learning curve and validate skills. In practice, a clear portfolio and demonstration of past findings will outweigh simple CV claims, so hands-on evidence is essential.
Getting started often means balancing unpaid practice with targeted paid projects until you build credibility. As you progress, you can focus on higher-value offerings such as source-code reviews, red team exercises, or long-term security consultancy.
Core Technical Skills You Must Master
To be effective and trusted, a freelance ethical hacker must master certain foundational skills. These include networking fundamentals, operating systems, web application security, scripting, and basic exploitation techniques. Learn how HTTP, cookies, authentication, and session management work, and become fluent in Linux and Windows internals.
Essential skillset
- Networking (TCP/IP, DNS, routing)
- Operating systems (Linux administration, Windows internals)
- Web security (OWASP Top Ten, API security)
- Scripting and automation (Python, Bash)
- Reverse engineering basics and malware hygiene
- Cloud security concepts (AWS, Azure, GCP fundamentals)
Practical labs, Capture The Flag (CTF) exercises and real-world practice are indispensable. If you prefer guided learning, many professionals follow organised courses that map skill modules to hands-on labs and projects.
Certifications and Formal Training
Certifications can speed client trust, especially early in your freelance career. Popular certifications include CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional), CompTIA Security+, and more specialised certs like OSWE or cloud-focused credentials. Certifications show commitment and can open doors to corporate contracts, but they do not replace demonstrable hands-on results such as pentest reports or bug bounty payouts.
Many freelancers combine certifications with instructor-led training from recognised institutes. If you want credentials plus practical lab time, consider programs that include mentor feedback and graded assessments for real validation. For local support and classroom options, you can explore available certification pathways that pair coursework with hands-on labs.
Build a Safe Home Lab and Portfolio
A home lab is your practice ground and a place to create proof-of-skill. Use virtual machines, intentionally vulnerable images (Metasploitable, OWASP Juice Shop), and isolated networks to learn safely. Document labs and produce writeups or blog posts that explain your methodology, findings, and remediation steps—these form the backbone of your portfolio.
What to include in your portfolio
- Pentest reports (redacted and permissioned)
- Bug bounty writeups with PoC screenshots
- CTF solutions and writeups
- Open-source tools or scripts you wrote
- Lab walkthroughs hosted on GitHub or your blog
Hiring managers and clients prefer practical evidence. If you’re new, start with volunteering small assessments for local non-profits or internal projects to build real-world case studies.
How to Find Clients and Platforms
Client acquisition mixes self-marketing and platform presence. Many freelancers begin on bug bounty platforms and crowdsourced sites, which provide a steady avenue for finding vulnerabilities and earning rewards. Over time move towards private contracts and recurring clients for stable income. Use multiple channels to diversify opportunities and reduce dependency on a single source.
Popular freelance channels include freelance marketplaces, security-focused job boards, direct outreach to startups, and participating on bug bounty platforms. If you are targeting corporate pentests, you may need to network with security managers and offer a professional contracting process including proposals, scoped statements, and sample reports.
Pricing, Contracts, and Scope Management
Setting fair prices and clear contracts is crucial. Decide whether you’ll charge hourly, per-project, or per-vulnerability. Hourly rates are common for small assessments and consultancy, while fixed project fees suit well-defined scopes. Bug bounties pay per valid finding but are unpredictable. Ensure your contracts include scope, exclusions, rules of engagement, deliverables, confidentiality, liability limits, and payment terms.
Typical contract elements
- Scope (assets, IP ranges, domains)
- Schedule and allowed testing hours
- Data handling and non-disclosure terms
- Liability cap and indemnity clauses
- Retesting and remediation verification
Use clear, professional proposals and avoid ambiguity. Clients value a polished report and clear remediation steps as much as vulnerability discovery.
Tools, Workflow and Reporting
Build a reliable toolkit and repeatable workflow. Tools like Burp Suite, Nmap, Metasploit, Wireshark, and various scripting utilities will be part of your daily work. Automate reconnaissance and reporting tasks, but never substitute automation for manual verification. Reports should be structured with an executive summary, technical details, risk rating, PoC, and recommended fixes.
Good workflows include planning, reconnaissance, scanning, manual verification, exploitation (if in scope), reporting, remediation guidance, and retesting. Many freelancers adopt frameworks and templates to standardise output and save time between engagements.
Legal, Ethical and Professional Considerations
Operating ethically and legally is non-negotiable. Always obtain written permission before testing; follow responsible disclosure policies; and avoid exfiltrating or copying unnecessary sensitive data. Understand local laws and client compliance requirements such as data protection regulations. Reputation matters; unethical behaviour can end your freelance career quickly.
When engaging in bug bounty programs, carefully read program policies and stay within rules. For paid pentests, use a formal statement of work and ensure the client provides written authorisation and agrees to liability and confidentiality clauses.
Growing Your Freelance Business
Growth comes from consistent delivery, strong communication, and a visible track record. Publish writeups, contribute to open-source tools, speak at meetups, and maintain an active professional profile. High-quality reports, on-time delivery, and clear remediation advice generate referrals and repeat business.
Consider partnering with other freelancers to offer end-to-end services such as secure development consulting or long-term security program management. As you scale, invest in automation, client management tools, and perhaps subcontract junior testers under your brand.
Conclusion
Becoming a freelance ethical hacker is a practical path that blends technical skill, continuous learning, and professional discipline. Start with solid fundamentals, build a lab and portfolio, obtain useful certifications, and practise responsible disclosure. Use bug bounty platforms and direct client outreach to gain paid experience, and treat every report as a showcase of your capability. With consistent effort, transparency, and ethical conduct, you can build a rewarding freelance career in cybersecurity.
Frequently Asked Questions
Do I need a degree to become a freelance ethical hacker?
No. Many freelance ethical hackers are self-taught or come from non-degree backgrounds. Practical skills, a strong portfolio, and certifications often matter more than formal degrees.
Which certification is best for freelancers?
OSCP is highly regarded for practical offensive skills; CEH provides broad coverage. Choose certifications that align with your target market and the type of work you want to do.
What is the fastest way to start earning?
Participating in bug bounty programs and open-source security audits can generate initial earnings while you build a portfolio for paid pentest contracts.
How much can freelance ethical hackers earn?
Earnings vary widely based on skill, reputation, niche, and client type. Top freelancers and successful bug hunters can earn substantial incomes, but expect variability early on.
How do I keep client data safe?
Use encrypted storage, follow least-privilege principles, redact sensitive data in reports, and adhere to contractual confidentiality obligations.
Can I work full-time as a freelance ethical hacker?
Yes, many freelancers transition to full-time independent work. It typically requires building a steady client base or a reliable pipeline of bounty income.
Should I specialise or be a generalist?
Both paths work. Specialising in web apps, cloud, or IoT can command higher rates, while generalists can handle a broader range of projects.
How do I price my services?
Research market rates, factor in your expenses and time, and decide between hourly, per-project, or value-based pricing. Always include clear deliverables in the contract.
What tools should I learn first?
Start with Nmap, Burp Suite, Wireshark, and basic scripting in Python. These tools cover reconnaissance, web testing, and network analysis.
How important are soft skills?
Very important. Clear communication, report writing, and client management often determine whether a client returns or provides referrals.
How do I handle scope creep?
Set clear boundaries in the contract, log change requests, and issue amendments or additional quotes for work outside the original scope.
Is insurance necessary?
Professional liability insurance can protect you against claims arising from your services and is recommended for higher-risk engagements.
How do I get private pentest invites?
Build reputation through consistent quality reports, participate in public programs, and network with security teams and platform managers.
Where can I continue learning?
Follow hands-on courses, participate in CTFs, read vendor advisories, and consider training and mentorship programs from established providers to stay current.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0
















