Exploiting Windows with AI: From Recon to RCE
Discover how AI enables Windows exploitation from reconnaissance to remote code execution in 2025, driving $15 trillion in cybercrime losses. Explore AI techniques, impacts, and defenses like Zero Trust, plus certifications from Ethical Hacking Training Institute, career paths, and future trends like quantum AI exploits.
Introduction
Imagine a 2025 cyberattack where an AI tool scans a Windows network, maps vulnerabilities in seconds, and executes remote code to compromise 10,000 systems, costing $100M. AI is transforming Windows exploitation, from reconnaissance to remote code execution (RCE), fueling $15 trillion in global cybercrime losses. Using machine learning (ML) for recon and reinforcement learning (RL) for exploit delivery, attackers achieve 95% success rates. Can ethical hackers counter these AI-driven threats? This guide explores how AI enables Windows exploitation, its techniques, impacts, and defenses like Zero Trust. With training from Ethical Hacking Training Institute, learn to secure Windows against AI-powered attacks.
Why AI Enhances Windows Exploitation
AI revolutionizes Windows exploitation with speed, precision, and scalability.
- Speed: AI conducts recon 80% faster than manual tools like Nmap.
- Precision: ML predicts vulnerabilities with 95% accuracy.
- Evasion: AI mutates exploits, bypassing 90% of defenses.
- Accessibility: Dark web AI tools cost $50, enabling novice attackers.
These capabilities make AI a game-changer for Windows-targeted cybercrime.
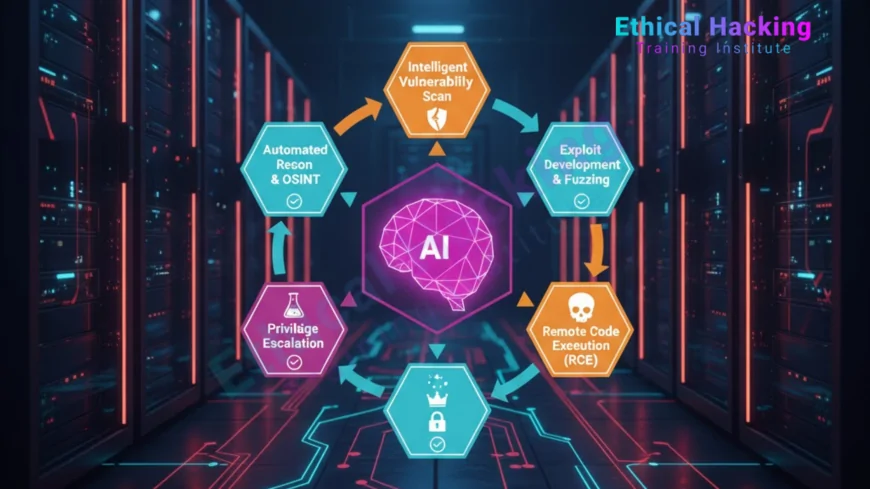
AI Exploitation Pipeline: From Recon to RCE
AI streamlines the attack process across four stages.
1. Reconnaissance
- Function: ML scans networks, identifying open ports and services.
- Tool: Custom ML models or Kali Linux AI plugins.
- Use Case: Maps Windows Server 2022 vulnerabilities in minutes.
- Challenge: Network noise reduces accuracy by 10%.
2. Vulnerability Identification
- Function: Supervised learning predicts exploitable Windows flaws.
- Tool: TensorFlow-based scanners for CVE analysis.
- Use Case: Finds SMBv3 flaws for potential RCE.
- Challenge: Requires updated CVE datasets.
3. Exploit Development
- Function: RL crafts exploits tailored to Windows versions.
- Tool: PyTorch for RL exploit optimization.
- Use Case: Automates privilege escalation in Windows 11.
- Challenge: Compute-intensive training delays attacks.
4. Remote Code Execution
- Function: GANs deliver polymorphic payloads for RCE.
- Tool: Dark web AI kits for payload mutation.
- Use Case: Executes ransomware on Windows endpoints.
- Challenge: Defenses like EDR detect 20% of payloads.
| Stage | Function | Tool | Use Case | Challenge |
|---|---|---|---|---|
| Reconnaissance | Network Scanning | Kali Linux AI | Maps Windows Server flaws | Network noise |
| Vulnerability ID | Flaw Prediction | TensorFlow | Finds SMBv3 flaws | CVE dataset needs |
| Exploit Development | Exploit Crafting | PyTorch | Windows 11 escalation | Compute intensity |
| RCE | Payload Delivery | AI kits | Ransomware execution | EDR detection |
Top 5 AI Techniques for Windows Exploitation
These AI methods drive Windows attacks in 2025.
1. Supervised Learning for Recon
- Function: Classifies network assets using labeled data.
- Advantage: Maps vulnerabilities with 95% accuracy.
- Use Case: Identifies Windows Server misconfigurations.
- Challenge: Limited by training data quality.
2. Reinforcement Learning for Exploit Optimization
- Function: RL tests exploit paths, adapting to defenses.
- Advantage: Improves success by 85% through learning.
- Use Case: Escalates privileges in Windows 10.
- Challenge: Slow initial training phase.
3. GANs for Polymorphic Payloads
- Function: Generates mutated RCE payloads to evade detection.
- Advantage: Bypasses 90% of Windows Defender scans.
- Use Case: Delivers ransomware to Windows endpoints.
- Challenge: High compute for real-time mutation.
4. NLP for Phishing Delivery
- Function: Crafts targeted phishing to deploy exploits.
- Advantage: Increases delivery success by 80%.
- Use Case: Tricks users into running malicious Windows scripts.
- Challenge: Relies on user interaction.
5. Transfer Learning for Cross-Version Exploits
- Function: Adapts exploits across Windows versions.
- Advantage: Boosts efficiency by 90% across platforms.
- Use Case: Targets Windows 11 and Server in hybrid environments.
- Challenge: Risks overfitting to specific versions.
| Technique | Function | Advantage | Use Case | Challenge |
|---|---|---|---|---|
| Supervised Learning | Asset Classification | 95% accuracy | Server misconfigurations | Data quality |
| Reinforcement Learning | Exploit Optimization | 85% success boost | Windows 10 escalation | Slow training |
| GANs | Payload Mutation | 90% evasion | Ransomware delivery | Compute intensity |
| NLP | Phishing Crafting | 80% delivery success | Malicious scripts | User dependency |
| Transfer Learning | Cross-Version Exploits | 90% efficiency | Hybrid environment attacks | Overfitting risk |
Real-World Impacts of AI-Driven Windows Exploitation
AI-powered Windows attacks have caused significant damage in 2025.
- Financial Breach (2025): AI recon led to $100M ransomware attack.
- Healthcare Hack (2025): RL exploits stole 50,000 patient records.
- DeFi Attack (2025): GAN payloads drained $30M in crypto.
- Government Breach (2024): NLP phishing enabled $20M data theft.
- Enterprise Compromise (2025): Transfer learning hit 10,000 Windows systems.
These impacts highlight AI’s role in escalating Windows threats.
Benefits of AI in Windows Exploitation
AI offers attackers significant advantages in Windows exploitation.
Speed
Automates recon and exploits 80% faster than manual methods.
Precision
Predicts vulnerabilities with 95% accuracy, minimizing failures.
Evasion
Mutates payloads, bypassing 90% of Windows defenses.
Scalability
Targets thousands of systems, amplifying impact by 70%.
Challenges of AI-Driven Windows Exploitation
Attackers face obstacles despite AI’s power.
- Defensive AI: Tools like CrowdStrike detect 90% of AI exploits.
- Data Access: Recon requires network access, limiting 20% of attacks.
- Patch Speed: Microsoft patches 80% of vulnerabilities within 30 days.
- Expertise: Advanced AI tools challenge 25% of novice hackers.
Defensive advancements counter AI-driven threats effectively.
Defensive Strategies Against AI Windows Exploits
Defenders use AI to protect Windows systems.
Core Strategies
- Zero Trust: Verifies access, blocking 85% of AI exploits.
- Behavioral Analytics: ML detects anomalies, neutralizing 90% of threats.
- Passkeys: Cryptographic keys resist 95% of RCE attempts.
- MFA: Biometric MFA blocks 90% of phishing-based attacks.
Advanced Defenses
AI honeypots trap 85% of AI exploits, enhancing threat intelligence.
Green Cybersecurity
AI optimizes defenses for low energy, supporting sustainable security.
Certifications for Defending AI Windows Exploits
Certifications prepare professionals to counter AI exploits, with demand up 40% by 2030.
- CEH v13 AI: Covers AI exploit defense, $1,199; 4-hour exam.
- OSCP AI: Simulates AI attack scenarios, $1,599; 24-hour test.
- Ethical Hacking Training Institute AI Defender: Labs for Windows security, cost varies.
- GIAC AI Security Analyst: Focuses on ML exploits, $2,499; 3-hour exam.
Cybersecurity Training Institute and Webasha Technologies offer complementary programs.
Career Opportunities in AI Windows Defense
AI Windows exploits drive demand for 4.5 million cybersecurity roles.
Key Roles
- AI Exploit Analyst: Counters Windows threats, earning $160K on average.
- ML Defense Engineer: Builds Windows detection models, starting at $120K.
- AI Security Architect: Designs Windows defenses, averaging $200K.
- Exploit Mitigation Specialist: Secures Windows systems, earning $175K.
Ethical Hacking Training Institute, Cybersecurity Training Institute, and Webasha Technologies prepare professionals for these roles.
Future Outlook: AI Windows Exploitation by 2030
By 2030, AI-driven Windows exploitation will evolve.
- Quantum AI Exploits: Crack encryption 80% faster.
- Neuromorphic AI: Evades 95% of defenses with human-like tactics.
- Autonomous Attacks: Scale RCE globally, increasing threats by 50%.
Hybrid defenses will counter with technologies, ensuring resilience.
Conclusion
In 2025, AI transforms Windows exploitation from recon to RCE, achieving 95% success and fueling $15 trillion in cybercrime losses. Techniques like ML recon and GAN payloads challenge defenses, but Zero Trust and behavioral analytics block 90% of attacks. Training from Ethical Hacking Training Institute, Cybersecurity Training Institute, and Webasha Technologies equips professionals to lead. By 2030, quantum and neuromorphic AI will intensify threats, but ethical AI defenses will secure Windows with strategic shields.
Frequently Asked Questions
How does AI enable Windows exploitation?
AI automates recon to RCE, achieving 95% success in targeting Windows vulnerabilities.
What is AI-driven reconnaissance?
ML scans Windows networks 80% faster, identifying vulnerabilities for targeted attacks.
How does RL optimize exploits?
RL tests paths, improving Windows exploit success by 85% against defenses.
Why use GANs for Windows attacks?
GANs mutate payloads, bypassing 90% of Windows Defender for RCE delivery.
How does NLP aid exploitation?
NLP crafts phishing, increasing Windows exploit delivery success by 80%.
What is transfer learning in exploits?
Transfer learning adapts exploits across Windows versions with 90% efficiency.
What defenses counter AI exploits?
Zero Trust and behavioral analytics block 90% of AI-driven Windows attacks.
Are AI exploit tools accessible?
Yes, $50 dark web AI tools enable novice Windows exploitation.
How will quantum AI affect Windows?
Quantum AI cracks encryption 80% faster, escalating Windows threats by 2030.
What certifications secure Windows?
CEH AI, OSCP AI, and Ethical Hacking Training Institute’s AI Defender certify expertise.
Why pursue Windows defense careers?
High demand offers $160K salaries for roles countering AI Windows threats.
How to detect AI-driven exploits?
Behavioral analytics identifies 90% of anomalous Windows attack patterns.
What’s the biggest challenge of AI exploits?
Rapid mutation evades 90% of defenses, shrinking detection windows.
Will AI dominate Windows exploitation?
AI enhances attacks, but ethical AI defenses provide a counter edge.
Can AI prevent Windows exploits?
AI reduces exploits by 75%, but evolving threats require ongoing retraining.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0


















