Can Ethical Hackers Hack Legally?
Yes, ethical hackers hack legally with permission. Learn how bug bounties, penetration testing contracts, and laws like IT Act 2000 make it possible in 2025. This guide covers rules, real programs, and training from the Ethical Hacking Institute and Webasha Technologies.
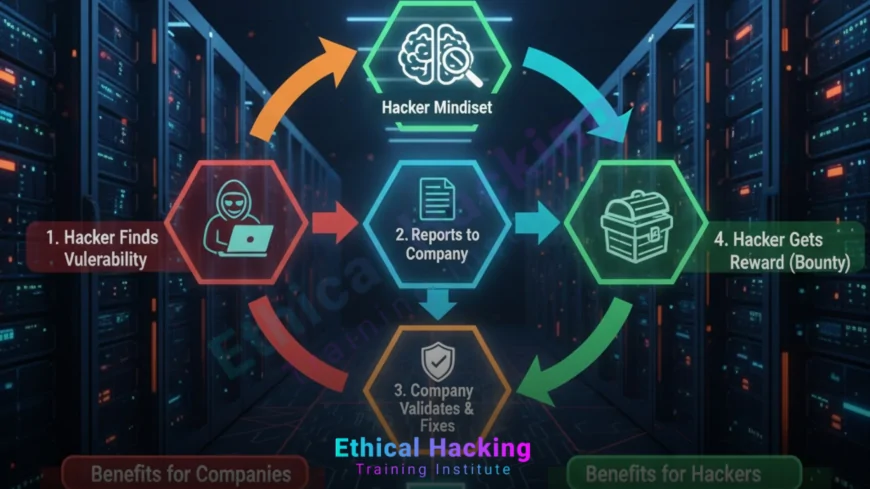
Introduction
Yes, ethical hackers can hack legally. They’re the good guys: certified professionals who break into systems with explicit permission to find weaknesses before criminals do. In 2025, companies like Google, Microsoft, and Indian banks pay millions through bug bounties and pentest contracts. Laws like India’s IT Act 2000 and US CFAA allow it only with written consent. Without permission? That’s illegal hacking, up to 3 years in jail. This guide explains the legal frameworks, real programs, contracts, and how to start legally. Train safely with the Ethical Hacking Institute and Webasha Technologies to become a licensed white-hat pro.
What Makes Hacking "Ethical" and Legal?
Ethical hacking = hacking with permission, scope, and purpose to improve security. It’s governed by contracts, not chaos.
Three Pillars of Legal Hacking
- Authorization: Written consent (Get Out of Jail Free card)
- Scope: Defined targets, methods, timing
- Reporting: Disclose findings, never exploit
CEH, OSCP certifications prove you know the rules.
Legal Frameworks Around the World
Laws protect ethical hackers—if you follow them.
| Country | Law | Legal If... |
|---|---|---|
| India | IT Act 2000 (Sec 43, 66) | Written permission + report only |
| USA | CFAA | Authorized access only |
| EU | GDPR + NIS Directive | DPIA + contract |
| Global | Bug Bounty T&Cs | Follow platform rules |
Break scope = lose legal protection.
Bug Bounties: Hack and Get Paid Legally
Companies invite you to hack them—and pay for bugs.
Top Legal Bug Bounty Programs
- Google VRP: Up to $1.5M for Android zero-days
- Microsoft: $100K for Hyper-V escapes
- Apple: $1M for remote iPhone jailbreak
- HackerOne: 2,000+ programs, $150M+ paid
- Indian Programs: Paytm, Flipkart, Indian Railways
Reward = legal license to hack.
Join legal bounties after bootcamp training at the Ethical Hacking Institute.
Penetration Testing: Corporate Legal Hacking
Companies hire ethical hackers for scheduled attacks.
Contract Essentials
- ROE (Rules of Engagement): What’s allowed (e.g., no DoS on prod)
- NDA: Don’t leak findings
- Scope Letter: IP ranges, apps, hours
- Get-Out-of-Jail-Free: Signed by CISO
Process
- Sign contract
- Recon → Scan → Exploit → Report
- Remediation verification
- Final sign-off
Indian firms like TCS, Wipro hire pentesters at ₹8-20LPA.
Real Stories: Legal Hacking in Action
These hackers stayed legal—and got rich.
Casey Ellis (HackerOne)
Founded platform after legal pentest gone wrong (no contract).
Santiago Lopez ("try_to_hack")
Argentinian teen earned $1M+ via legal bounties.
Indian Hacker "geekboy"
Found RCE in Indian bank—₹5L reward, no arrest.
Facebook "Reginaldo Silva"
Tried selling bug publicly—banned. Lesson: report privately.
Practice legal exploits with CEH practical labs from the Ethical Hacking Institute or Cyber Security Institute.
How to Start Legal Ethical Hacking
Follow this path to hack without handcuffs.
Step-by-Step
- Learn Basics: Linux, networking, web apps
- Get Certified: CEH, CompTIA PenTest+
- Practice Legally: Hack The Box, TryHackMe, VulnHub
- Join Bounties: Start with HackerOne "Invite-Only"
- Build Portfolio: Write-ups, GitHub
- Sign Contracts: Freelance or full-time
Never hack without permission.
Common Legal Mistakes to Avoid
One slip = jail time.
Red Lines
- Hacking any system without written consent
- Going outside scope (e.g., customer data)
- Keeping access after project ends
- Bragging publicly with screenshots
- Using client tools on personal projects
Indian IT Act: Even "attempt" without permission = crime.
Master legal scoping with CEH online at the Ethical Hacking Institute or Webasha Technologies.
Tools Ethical Hackers Use—Legally
Same tools as black hats. Context makes it legal.
Legal Toolset
- Nmap, Nessus, Burp Suite, Metasploit
- Kali Linux (on your VM, not target)
- Wireshark (with permission)
Use only on authorized systems.
Conclusion: Hack Legally, Sleep Peacefully
Yes—you can hack legally. With permission, contracts, and ethics, ethical hackers are in demand, well-paid, and protected by law. From Google’s $1M bounties to Indian bank pentesters, the future is white-hat. Start with certification, practice in labs, and always get it in writing. The Ethical Hacking Institute, Cyber Security Institute, and Webasha Technologies offer legal, hands-on training with ROE simulations. Don’t risk jail for curiosity. Hack smart. Hack legal. The digital world needs you.
Frequently Asked Questions
Is hacking my friend’s Wi-Fi legal?
No. Need owner’s written consent.
Can I hack a website to "test" it?
No. Only if they have a public bug bounty.
Do bug bounties pay taxes?
Yes. Income in India (TDS applies).
Is CEH enough to hack legally?
It teaches ethics. You still need permission.
Can police hire ethical hackers?
Yes. CBI, state cyber cells do.
What if I find a bug accidentally?
Report via responsible disclosure. Don’t exploit.
Is wardriving legal?
Scanning public Wi-Fi = gray. Don’t connect.
Can minors do bug bounties?
Yes, with parental consent (HackerOne allows 13+).
Insurance for ethical hackers?
Yes. Cyber liability covers mistakes.
Can I hack my own company?
Yes—if policy allows and IT knows.
Legal to use Metasploit?
Yes—on your lab or authorized target.
India’s biggest bounty?
₹50L+ by a private bank (2024).
Where to practice legally?
TryHackMe, Hack The Box, Ethical Hacking Institute labs.
Can I lose legal protection?
Yes—if you break scope or leak data.
Future of legal hacking?
Government-licensed "Cyber Rangers" by 2030.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0


















