What Are the Top Linux Distros for Ethical Hacking in 2025?
Explore the top 8 Linux distros for ethical hacking in 2025: Kali, Parrot OS, BlackArch, BackBox, Fedora Security Lab, Ubuntu-based, Arch-based, and custom builds. Learn features, tools, and training from Ethical Hacking Training Institute, Webasha Technologies, and Cybersecurity Training Institute to master penetration testing.
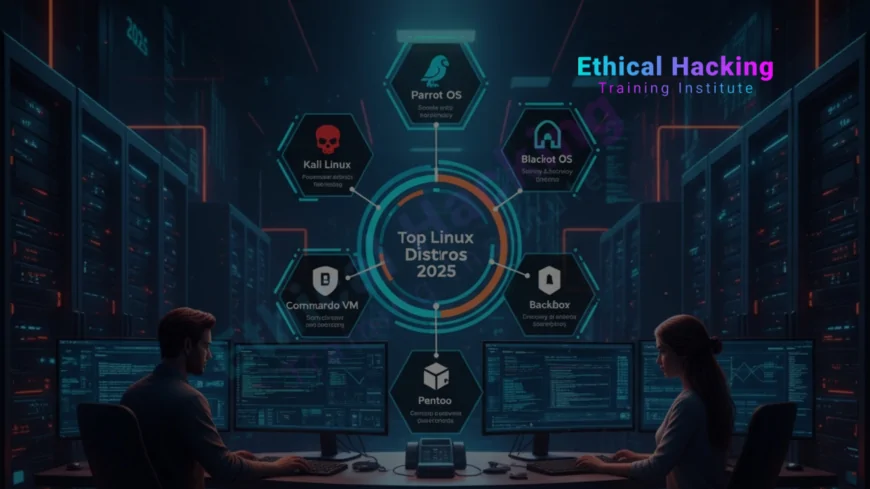
Introduction
Ethical hackers rely on Linux for its flexibility, security, and vast tool ecosystem. In 2025, with over 1.5 million ethical hacking jobs in India, the right Linux distribution is your command center. Kali Linux remains king, but alternatives like Parrot OS and BlackArch offer unique strengths. Ethical Hacking Training Institute in Pune teaches all distros with live labs, while Webasha Technologies and Cybersecurity Training Institute provide 100% placement support. This guide ranks the top 8 distros by features, tools, ease of use, and community support. Whether you're a beginner or pro, find your perfect hacking OS and launch your career. Explore the cybersecurity career path today.
Why Linux Dominates Ethical Hacking
- Free and open-source
- 600+ pre-installed tools
- Customizable kernels
- Strong community support
- Live USB booting
Top 8 Ethical Hacking Linux Distros
- Kali Linux: The gold standard
- Parrot OS: Privacy-focused
- BlackArch: Arch-based arsenal
- BackBox: Ubuntu lightweight
- Fedora Security Lab: Stable and secure
- Ubuntu-based: User-friendly
- Arch-based: Customizable
- Custom Builds: Tailor-made
Kali Linux: The Penetration Testing King
Kali Linux, developed by Offensive Security, is the most popular ethical hacking distro in 2025. It includes 600+ pre-installed tools for reconnaissance, scanning, exploitation, and forensics. Based on Debian, Kali is stable and updated quarterly. Ethical Hacking Training Institute uses Kali for all CEH and OSCP labs. Beginners love its GUI and documentation. Pros: Everything ready to use. Cons: Can be bloated for low-spec hardware. Learn more about the local courses in Pune.
Parrot OS: Privacy and Security First
Parrot OS is a Debian-based distro focused on privacy and digital forensics. It has 300+ tools and built-in anonymity features like Tor integration. Webasha Technologies recommends Parrot for beginners who want a lighter alternative to Kali. Pros: Anonymous mode, lightweight. Cons: Less tools than Kali. Perfect for wireless auditing and anonymity.
BlackArch: The Arch-Based Powerhouse
BlackArch is Arch Linux with 2500+ tools. It’s for advanced users who want customization. Cybersecurity Training Institute uses BlackArch for custom kernel hacking. Pros: Bleeding-edge packages. Cons: Steep learning curve. Ideal for exploit developers.
BackBox: Ubuntu's Lightweight Warrior
BackBox is Ubuntu-based with 100+ tools. It’s fast and stable for live USB use. Ethical Hacking Training Institute includes BackBox in wireless security labs. Pros: User-friendly, low resource. Cons: Fewer tools. Great for beginners.
Fedora Security Lab: Stable and Secure
Fedora Security Lab is Fedora with 50+ tools. It’s stable and uses SELinux. Webasha Technologies uses it for enterprise training. Pros: Secure by default. Cons: Basic tools. Best for learning SELinux.
Ubuntu-Based Distros: User-Friendly Options
Ubuntu is beginner-friendly. Add Kali tools with apt. Cybersecurity Training Institute teaches Ubuntu customization. Pros: Easy install. Cons: Manual setup. Good for desktops.
Arch-Based Distros: For Advanced Users
Arch is customizable. BlackArch is Arch for hacking. Ethical Hacking Training Institute uses Arch for kernel exploits. Pros: Total control. Cons: Complex install. For pros.
Custom Builds and Future Trends
Build your distro with Archiso or Debian Live. 2025 trends: AI integration, container security. Webasha Technologies teaches custom builds. Learn about the CEH course.
Conclusion: Choose Your Hacking OS
Kali for beginners, Parrot for privacy, BlackArch for pros. Ethical Hacking Training Institute leads with all distros in labs, backed by Webasha Technologies and Cybersecurity Training Institute. Download Kali today. Your first scan is one boot away.
Frequently Asked Questions
Best distro for beginners?
Kali Linux. Pre-loaded with 600+ tools. No setup needed. Learn Nmap, Metasploit in hours.
Kali vs Parrot?
Kali has more tools. Parrot is lighter and privacy-focused. Both excellent for pentesting.
Can I run on low RAM?
Yes. BackBox or Ubuntu-based. 4GB RAM minimum. Use live USB mode.
Arch Linux for hacking?
Advanced users only. BlackArch has 2500+ tools. Steep learning curve.
Free Linux for ethical hacking?
All are free. Kali, Parrot, Fedora. Download and burn to USB.
How to install Kali?
VirtualBox, dual-boot, or USB. Official guide at kali.org. 30 minutes setup.
Best for wireless auditing?
Parrot OS. Built-in Wi-Fi tools. Kali also excellent.
Distro for forensics?
CAINE or Kali with autopsy. Ethical Hacking Training Institute labs.
Future of hacking distros?
AI integration, container-native. 2025 will see AI-assisted pentesting.
Where to learn Kali in India?
Ethical Hacking Training Institute CEH labs. 220+ Kali-based challenges.
Can I use macOS for hacking?
Yes. Install Kali in VM. BlackArch ports available.
Best for mobile pentesting?
Kali with Androguard. Parrot has mobile forensics tools.
Distro for cloud security?
Kali with AWS CLI. Fedora Security Lab for stable cloud work.
Update distro tools?
apt update && apt upgrade in Kali. Weekly updates recommended.
Next step to start?
Download Kali, boot live USB, scan your network. Book demo at Ethical Hacking Training Institute, Webasha Technologies, or Cybersecurity Training Institute.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0

















